BeyondTrust. 5 Use Cases for Reducing Unix & Linux Attack Surfaces and Achieving Compliance
The concept of least privilege roughly states that all users, applications, and processes should only be granted access to the minimum data and resources they need to perform their job, and for the least time necessary. In many cases, this equates to standard user access.
However, many basic OS, management, application, and software functions (e.g. configuration utilities) for Unix and Linux platforms require more than just standard privileged access. Traditionally, this required end users to possess elevated privileges in the form of root or administrative usernames and passwords. To overcome this inherent security and compliance risk, organizations must remove the need to distribute and maintain root and administrative credentials. That’s where third-party commercial Unix/Linux privilege management solutions come in. Enterprise-class solutions offer multiple benefits over native Unix/Linux capabilities and open-source tools like sudo.
But where do you start with Unix/Linux privilege management?
How do you know what to tackle first? BeyondTrust’s 30+ years in pioneering the Unix/Linux least privilege market tells us you can reduce Unix/Linux attack surfaces and improve compliance by doing five basic things really well. I’ve mapped some key capabilities in our Privilege Management for Unix & Linux product to these use cases.
1) Remove the need to log in as root
Many system and application users of Unix and Linux use the phrase, “I need root,” declaring they can only perform their daily job functions if they can log on as “root”, the most powerful user on the system. Root is often referred to as the “God” user as there is little the root user cannot do.
Allowing usage of the root account complicates the ability to audit an individual’s actions (promoting account sharing) and inhibits the use of a strong, changeable password for the root account due to the need for multiple identities to use the account at any given time. These characteristics dramatically increase risk. The organization faces a heightened danger from insider threats via malicious and accidental behaviors, as well as additional exposure from external threats due to weak and non-changing passwords. There is zero accountability when using root to perform administrative functions.
Privilege Management for Unix & Linux implements a true least privilege delegation model. The product enables users to run any command at a higher privilege level, so long as it is allowed by a policy defined in the centralized policy server. Removing the need for users to logon as root enables much tighter security controls around the root user account. Integrating a privileged password management system, such as BeyondTrust Password Safe, layers on further security and productivity benefits by proactively vaulting and managing these credentials.
Privilege Management for Unix & Linux does not rely on open-source privilege escalation tools like sudo, thereby further reducing the risk of critical vulnerabilities.
2) Consolidate logs and make the data accessible quickly and efficiently
It’s well-established that the command line nature of Unix and Linux systems doesn’t lend itself to easily-consumed searching capabilities. This drawback becomes especially apparent in very large enterprise systems with multiple log servers concurrently running. With that said, consolidating vast amounts of data, and finding what you are looking for, is key in identifying mistakes and mitigating risk.
BeyondTrust solves this problem via a powerful integration between Privilege Management for Unix and Linux and ElasticSearch/Logstash. This integration empowers customers to zero in on what they seek, quickly and efficiently. Privilege Management for Unix & Linux sends log data to ElasticSearch, where it is indexed in near real-time. The indexed data is searchable from within our dedicated management platform.
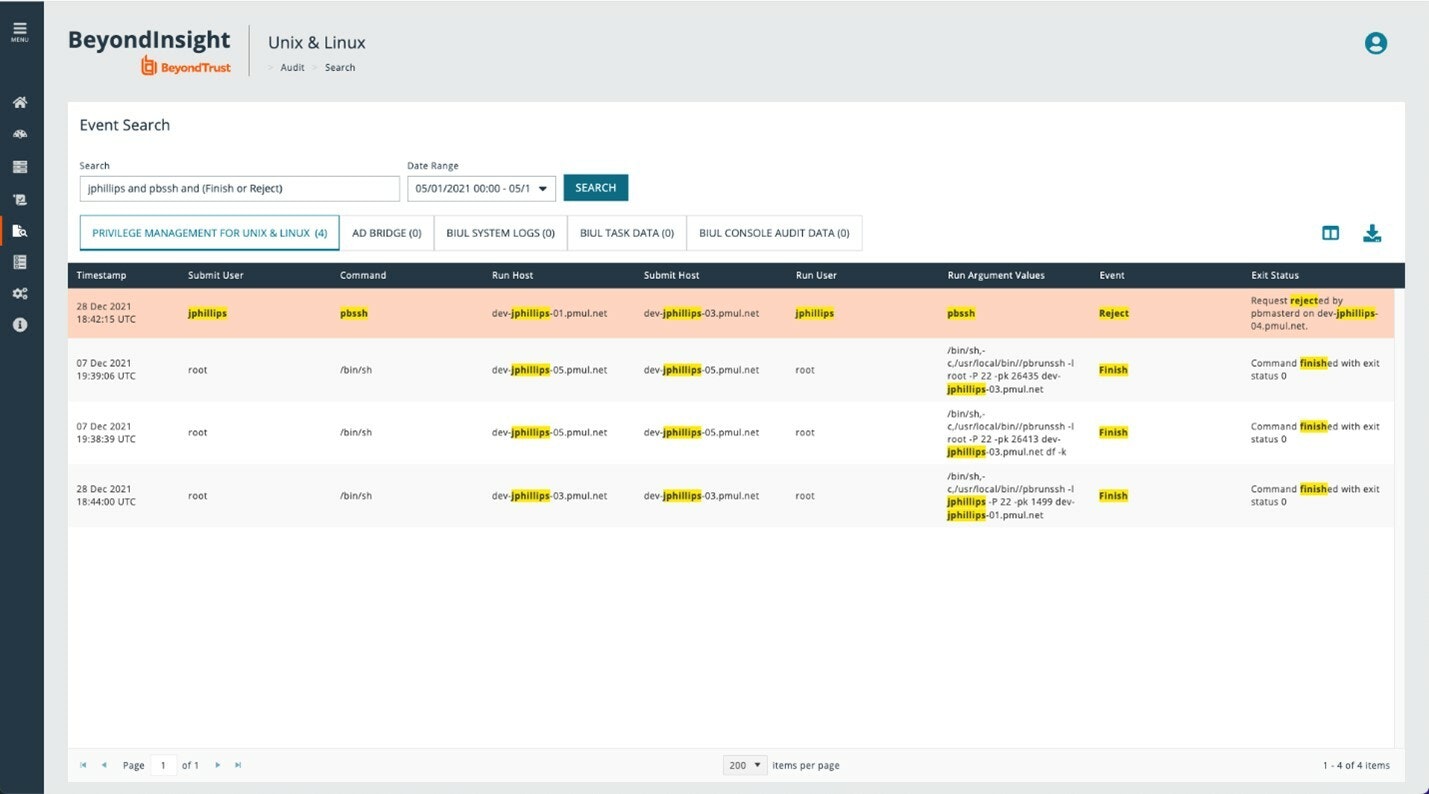
The unified search interface allows customers to search PMUL log data in an easy-to-use, “Google like” search interface. While the search syntax can be simple, it also provides advanced search capabilities. Advanced search features include Logical operators (and/or) Precedence, Wildcard searching, Field-specific searching, and/or Exact match searching using double quotes, and more. IT stakeholders benefit from having real-time visibility into the state of privilege-related Unix and Linux risks at their fingertips.
Privilege Management for Unix & Linux and AD Bridge (BeyondTrust’s solution for centralizing authentication for Unix/Linux environments by extension of AD’s Kerberos authentication and single sign-on capabilities) display the unified search results in bespoke grids. Titles will highlight the number of results for each product, and all search results will be highlighted in the grid and the details card. All results can be downloaded in either json or CSV format.
You can read more about this feature here.
3) Achieve compliance for the root account – indelible audit trail, unimpeachable logs
From time to time, the most senior admins will have a legitimate need to leverage root capabilities. These sensitive use cases may include certain types of system-level changes, or just reflect the ad-hoc nature of the commands the user may need to issue. One challenge is that compliance teams need to monitor ALL activity and ensure accountability for actions, especially considering the privilege level being used during these sessions. Compliance teams need to cleanly identify:
- who was using the root account
- when they were using the root account
- what activities were performed/commands typed by the root account.
It is also imperative to protect log files from any sort of tampering. Searching the log files is critical for enabling the compliance team to find what they are looking for quickly and efficiently.
Privilege Management for Unix & Linux allows standard-named user accounts to elevate their rights to root level, with full session logging and session replays, providing a centralized, indelible audit trail and ultimate accountability for each individual system administrator. A dedicated management platform delivers a powerful, unified search experience where all log files are consolidated and can be searched via its ElasticSearch integration.
4) Faster forensics, when time is of the essence
Logging all Unix/Linux user activity can quickly become untenable. When a forensic investigation needs to be performed, organizations can waste time and manpower performing investigations as the sheer amount of data that is generated can be overwhelming.
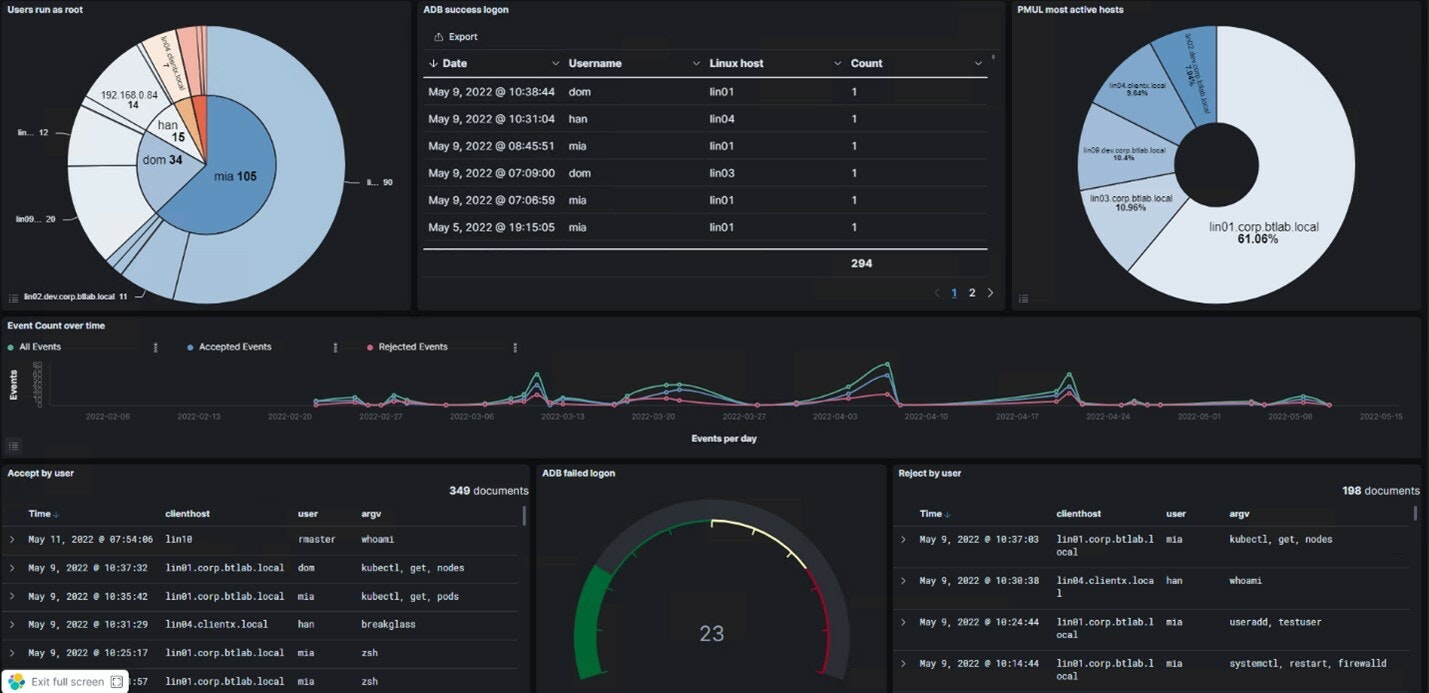
With Privilege Management for Unix & Linux, event logs can be dynamically named, centrally located, and access controlled in the central management console. Our product utilizes Elastic to index all recorded sessions, with all information accessible via command line or REST API. Data is indexed in near real-time so customers can build pro-active analytics using the built-in Kibana dashboard.
5) Record all Unix/Linux sessions – everything typed, everything seen
Least privilege is an ideal for most security groups, but sometimes, you just need to turn over a privileged shell, such as a root level shell. Strict auditing is a good way to keep honest people honest. So, for trusted admins, a full root shell is often no issue, as long as their activity is recorded in a tamperproof way to meet compliance needs.
One simple line in Privilege Management for Unix & Linux policy turns on full session recording, which is then dynamically named and automatically indexed using ElasticSearch. This capability enables organizations to view the session in many different ways:
- interactive playback
- video style playback
- session transcript
- command history
- searchable index (this capability provides flexibility to quickly turn on and search user activity, reducing risk).
How well are you performing each of these five activities now? What is standing in your way?
Time to retire (or supplement) sudo?
Sudo has been around for a long time. As the number of systems and users has grown, management of sudo has become very time-consuming, and completely untenable in even moderately complex environments. Coupled with limitations of the controls available in sudo, systems now seem overly exposed to an increasing number of internal and external security threats.
Privilege Management for Unix & Linux provides a far more flexible policy language, allowing for creation of infinitely more granular policies at both the command and system level. Privilege Management for Unix & Linux increases security in several ways, including moving the policy and log data off the users’ workstation or server, and utilizing the latest encryption technology for data both in transit and at rest.
The compliance and security benefits of using a commercial least privilege solution versus native sudo capabilities is significant. And for those organizations on a zero trust journey, the BeyondTrust solution provides must-have security controls around Unix/Linux systems and administration.
As you consider how to improve the maturity of your Unix/Linux server security and compliance, consider the five use cases I discussed in this blog.
Source: BeyondTrust

