Sophos announces the SPAMPIONSHIP league highlighting the worst offending countries for spam
Every quarter Sophos announces the SPAMPIONSHIP league highlighting the worst…
What do IT managers rate as their #1 firewall issue today? Our survey says…
Back in the summer we ran a little survey on SpiceWorks and almost 400 Small…
Dropbox accounts breached. Ιs your data safe in the public cloud?
Dropbox usernames and passwords were leaked online this week. It’s the…
Sophos Strengthens Network Security Portfolio to Meet the Diverse Needs of Today’s Businesses
Sophos announced additions to its range of SG Series firewall/UTM appliances,…
Sophos Advances Cloud, Mobile, and Web Security with Acquisition of Mojave Networks
Sophos announced that it has acquired cloud-based security firm Mojave Networks…
Infocom World Caravel Hotel 21 Oct 2014
InfoCom World Congress is the largest event on digital technologies in SE…
With EU Data Protection Regulation on the horizon, will companies be ready?
A lot has changed since 1995, the last time a major European law…
Ipoque at Mobile World Congress 2013
a conference featuring prominent Chief Executives representing mobile…
Jacarta's Go-Probe Sensor range expanding!
coverage of your Jacarta solution by using Vibration Sensors with Adjustable…
Top 10 Reasons to Choose APV Series Application Delivery Controllers (ADCs)
Here are the Top 10 reasons to choose Array's APV Series Application…
OpenSSL Heartbleed, what is it and what does it mean for security?
We also found out that the Heartbleed bug is in a version of the OpenSSL…
10 tips for securing your smartphone
1. Always secure your smartphone with a password One of the most basic security…
Microsoft predicts bleak future for XP users after patches run out
One risk is that attackers will have the advantage over defenders who choose to…
How to deliver enterprise security for your SMB
And, as an IT professional, I faced the same challenge in all of these roles:…
Infographic: Timeline shows 10 years of mobile device malware (2004-2014)
The current total of 650,000+ pieces of Android malware is up by approximately…
Mike Valentine Named a Top IT Mid-Market Executive by CRN
This list was conceived to put a spotlight on the professionals driving one of…
GlobalSign Deepens Existing Partnership With Leading Scandinavian SSL Provider Through Strategic Share Investment
Through the partnership, both parties aim to meet the increasing demand…
Windows XP retirement: Using Sophos products to secure XP
So here are some tips on how you can use Sophos products to maintain security…
SEA hijacks Microsoft Twitter accounts, Xbox support blog and Technet
Syrian Eagle told Mashable that Microsoft deserves what it got because it's…
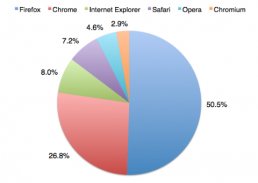
Firefox burns Chrome in our trustworthy browser poll
Our poll offered readers the chance to vote for one of the six most popular web…
NSS and SOPHOS @ Infocom Security 2013
information security to the status of the most crucial factor that should be…
What you need to know about the Bash “Shellshock” vulnerability
Although it can be exploited in some cases, the good news is that not all…
New Peplink Balance 2500 router and Updated Technology Pages
Learn How Balance and MAX Routers Team Up for Unbreakable VPNs The Balance…
Latest Free Version of Sophos Mobile Security Delivers Application Protection, Faster Scanning and Web Protection
An equally alarming industry statistic, users not running the most recent…
Sophos Email Appliance offers Enhanced Phishing Protection
Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) were both…
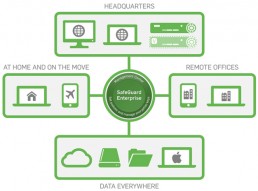
Encryption Without Compromise: The New SafeGuard Enterprise 6.1
With version 6.1 we’re addressing the two biggest issues in encryption…
Sophos Unleashes Strategy to Leverage the Cloud to Simplify Security and Enhance Protection
Easy to deploy and simple to manage, Sophos Cloud gives Sophos partners and IT…
Opera breached, has code cert stolen, possibly spreads malware - advice on what to do
"On June 19th we uncovered, halted and contained a targeted attack on our…
Sophos announced Sophos Mobile Control 4.0
The new Sophos solution helps IT professionals confidently implement BYOD…