Sophos. The problem with firewalls
There’s an evolution underway in firewalls that’s different from…
GlobalSign. Six Ways GDPR Will Affect HR
In May 2018, the EU will introduce a new set of data rules known as the…
Gartner acknowledges Sophos’ continued data protection leadership, again
After being recognized by Gartner as a leader in seven consecutive Magic…
Trustwave. Can Your Cloud Security Be Too Smart?
Many companies are transitioning to the cloud. Cloud services offer highly…
Sophos named Channelnomics Security Vendor of the Year, again
For the second year in a row, Channelnomics has named Sophos Security Vendor…
Sophos Intercept X is the Security Innovation of the year
The praise for Intercept X and its next-gen anti-ransomware, anti-exploit…
Boldon James. Data Classification as a Catalyst – Cloud Access Security Broker (CASB)
Cloud computing has forever changed the way many companies do business. With…
Intercept X is a Tech Innovator
Intercept X is a next-gen solution breaking the mold for IT security, and…
Sophos XG Firewall: delivering industry firsts
By staying focused on solving today’s problems with network security,…
CyberArk. 7 Types of Privileged Accounts You Should Know
Privileged accounts exist in many forms across an enterprise environment, and…
CyberArk. Countdown to GDPR. Protecting the Pathways to Personal Information
The General Data Protection Regulation (GDPR) goes into force on May 25, 2018,…
Sophos XG Firewall v17. Sleep easy.
v17 combines a breakthrough in network visibility with improvements to our…
Trustwave. How to Eliminate Common Sources of Employee Fraud
While you want to believe all your employees are loyal and trustworthy, many…
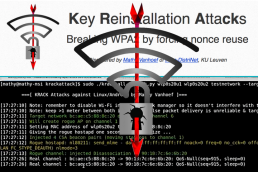
GlobalSign. KRACK Wi-Fi Vulnerability: What It Is and How to Protect Yourself
Users of seemingly everywhere Wi-Fi, free or otherwise, take note: a new flaw…
NSS and Sophos at the 19th Infocom World Conference, Wednesday 25 October 2017
The ICT sector, and Telecoms mostly, are considered to be the main…
Sophos Mobile 7.1 – secures company data and guards user privacy
Sophos Mobile 7.1 is now available and, with new features, it’s an even…
Boldon James. Data Classification in Healthcare
Healthcare is a highly competitive industry where payers and providers are…
Sophos XG Firewall v17 Release Candidate is out now!
A special thank you to all of you who have been actively participating in the…
GlobalSign Announces CloudSSL Offering for SaaS Providers
GlobalSign (www.globalsign.com), a leading provider of identity and security…
CyberArk. Get Your Enterprise Ready for GDPR
The General Data Protection Regulation (GDPR) is said to be one of the most…
Boldon James. Data Classification as a Catalyst - Encryption
There is little doubt that encryption is a very powerful tool whose inclusion…
SealPath and Boldon James Partner on Document Security Classification & Protection
Boldon James, the leading provider of data classification and secure messaging…
IDC GDPR Workshop (with speakers from Sophos and CyberArk) - Addressing the Challenges and Getting Compliant
On September 26, 2017, IDC organizes the GDPR Workshop - Addressing the…
Sophos Mobile: iOS 11 and Android Oreo ready, already
With iOS 11 releasing to the public today, and Android 8.0 Oreo made available…
Boldon James. 5 tips for achieving GDPR compliance
The European General Data Protection Regulation will have a global impact when…
Sophos XG Firewall v17 is nearly here
The highly anticipated public beta for Sophos XG Firewall v17 is now underway…
Boldon James. Data Classification as a Catalyst for Data Retention and Archiving
Businesses manage data retention in a multitude of ways for many different…
SophosLabs. Ransomware families, and how to fight them
Ransomware has been with us for a while now and is even considered old news by…
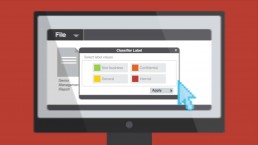
Boldonjames. Data Classification as a Catalyst for DLP
Data Loss Prevention (DLP) is different from most traditional data-centric…
CyberArk Cited by Gartner in Privileged Access Management Market Guide for Fourth Year in a Row
CyberArk, the company that protects organizations from cyber attacks that have…