GlobalSign. Tips to Browsing the Internet Safely without Being Tracked
Protecting your online anonymity is no piece of cake. After all, today’s…
SC Media awards Sophos XG Firewall the full five stars
“This demands your attention no matter what size your…
GlobalSign. How to Spot a Phishing Website
Phishing isn’t an unfamiliar term in these parts. In a previous blog…
Sophos. Protecting the treasure trove
Ransomware has been on the computer security radar for some time now but are…
Sophos. What makes a great firewall?
We know that a firewall is the first line of defense against external threats.…
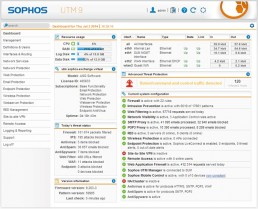
Sophos. UTM 9.5 is on its way
UTM 9.5, including many new features you’ve asked us for, is just around…
CyberArk. Your Greatest Threat Might Already Be Inside Your Network
Insider activity—both malicious and simple error—accounts for a…
Sophos. Best practice lays the foundation for defence
In the UK we have recently seen lots of headlines about cyber security and…
Hunting Privileged Account Vulnerabilities with CyberArk Discovery & Audit (DNA)
It’s widely understood that cyber intruders and internal threat actors…
NSS, Sophos, Cyberark and Sealpath at the 7th Infocom Security Conference, 29-30 March 2017
For one more year, NSS has a strong presence at the 7th Infocom Security…
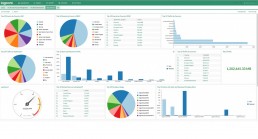
Releasing LogPoint 5.6.0
LogPoint is proud to announce LogPoint 5.6!Since the last large upgrade back…
Corero. IoT Security Is an Oxymoron
The Internet of Things (IoT) continues to be a boon to hackers and a bane to…
Sophos. Why you should put your staff to the test with phishing drills
When Sophos Phish Threat was released in January, we pointed out that: Email…
Corero: If You Haven’t Already Been DDoS’ed, Assume You Will Be
It’s no secret these days that cyber threats are rampant and varied.…
Sophos. Anti-malware is imperfect but still necessary. Here’s why.
Doctors sometimes make mistakes that harm the patient. Police often fail to…
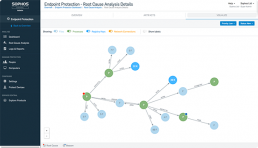
Sophos Endpoint Exploit Prevention. Block Ransomware with the Power of Intercept X
The protection capabilities of Intercept X are now available to Endpoint…
Corero: The Importance of DDoS Attack Visibility
The field of cyber forensics is getting much more attention lately, mostly…
Corero: Nearly 40% of Companies Lack Skills and Technology to Handle DDoS Attacks
A recent TripWire study highlights the growing problem of cyberattacks, and…
Detecting Ransomware with LogPoint
Ransomware is doubtless a rising threat nowadays, putting all small,…
SophosLabs malware forecast points to rising IoT threats, more ransomware
SophosLabs has released a malware forecast to coincide with the start of RSA…
Sophos Adds Advanced Machine Learning to Its Next-Generation Endpoint Protection Portfolio with Acquisition of Invincea
Sophos, a global leader in network and endpoint security, today announced it…
CyberArk: Don’t Analyze Everything - Analyze the Right Thing to Detect and Respond to Insider Threats
In 2013, organizations worldwide started to take insider threats seriously,…
Corero: DDoS Attacks Won't Be Blocked by Black Holing/Null Routing
Distributed denial of service (DDoS) attacks have been around since the early…
CyberArk: When Innocent Mistakes Turn Into Costly Problems
When most people hear about an “insider threat,” they often assume…
Sophos Mobile Security wins the AV-TEST Best Android Security Award
After posting an unprecedented and unbroken streak of perfect test scores in…
Sophos is a leader in Gartner Magic Quadrant for Endpoint Protection Platforms
We’re excited to share that Sophos has been named a leader in the 2017…
Introducing Sophos Phish Threat: the world’s easiest-to-use attack simulator
Our mission at Sophos is to provide the best security solutions on the market…
Increased Risks of DDoS Attacks for Ransom to Businesses
In recent weeks, the UK retail bank Lloyds was hit with a denial of service…
The challenges and opportunities for managing the Internet of Things
The Internet of Things (IoT) has been in the news lately for facilitating…
Don’t get held hostage by ransomware. Head over to the Sophos Anti-Ransomware Hub
According to official data, in 2016 alone, hackers have taken over $1 Billion…