Sophos Firewall named best network security solution by CRN®
We’re thrilled to announce that Sophos Firewall has been named the best network…
Sophos earns perfect scores in SE Labs endpoint protection report
We’re delighted to share that Sophos endpoint security products ranked as…
Sophos 2023 Threat Report: the continued evolution of “Crime-as-a-Service”
Maturing marketplaces, capabilities-for-hire continue to proliferate…
Sophos Firewall v19.5 is now available
Sophos Firewall OS v19.5 is a free upgrade for all licensed Sophos Firewall…
Sophos MDR: Results from the first MITRE Engenuity™ ATT&CK Evaluation for Security Service Providers
Sophos MDR recorded an exceptional performance with results that validate our…
SealPath.The real impact of ransomware on businesses
A few years ago we saw how a new wave and trend in ransomware attacks. In the…
NSS at Europe’s biggest cybersecurity expo/congress IT-SA EXPO&CONGRESS
IT-SA EXPO&CONGRESS IS EUROPE'S LARGEST TRADE FAIR FOR IT SECURITY...…
Fortra. The new face of HelpSystems
HelpSystems announced today that it has become Fortra™ a name synchronous with…
Datto. What is Managed SOC (Security Operation Center)? Why MSPs need MDR
Hackers have a deep playbook for penetrating networks. Even when managed…
Sophos MDR Launches Compatibility with Third-Party Cybersecurity Technologies
I am thrilled to announce the launch of new third-party security technology…
Sophos Firewall Recognized as a Strong Performer in The Forrester Wave™: Enterprise Firewalls, Q4 2022
Sophos received the highest possible rating in the Product Vision, Execution…
Automatic Upgrade to Sophos MDR Complete for Existing Customers
We’ve expanded our Managed Detection and Response service (originally called…
BeyondTrust. Insider Threat Indicators: How to Mitigate Insider Attacks (Part 2)
How to prevent data leakage from insider attacks Insider threats involve…
BeyondTrust. Insider Threat Indicators: How to Identify Insider Attacks (Part 1)
What is an insider threat? An insider threat is an internal persona acting as…
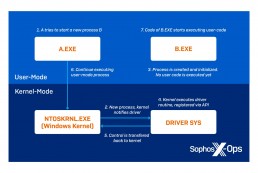
Sophos. BlackByte ransomware gang adds sophisticated “Bring Your Own Driver” technique to bypass more than 1,000 drivers used by EDR products
Sophos, a global leader in next-generation cybersecurity, today announced that…
MailStore V22.3: Support for Outlook 2021, More Security, and a Better User Experience
This quarter too, we’re happy to present a new version of our software for…
Sophos. Top Five Reasons to Use MDR Services
The reality is that technology solutions alone cannot prevent every…
Sophos. The State of Ransomware in State and Local Government 2022
We’ve just released the State of Ransomware in State and Local Government 2022…
Sophos ZTNA v1.1 now available
Sophos Zero Trust Network Access is now available with gateway support for the…
Sophos. The State of Ransomware in Retail 2022
The retail sector is no exception when it comes to the growing ransomware…
DattoCon22 was a great success and NSS was there
Kaseya, the leading global provider of unified IT management and security…
Datto. Top Tips for Cybersecurity Regulatory Compliance
Did you know that human mistakes are to blame for 95% of all cybersecurity…
Sophos. The importance of zero trust network access (ZTNA) in healthcare
With perimeter boundaries quickly blurring thanks to remote care and…
HelpSystems. Enterprise Data Security: Why It Matters and How To Build a Strategy
Before trying to better understand what enterprise data security is, it’s best…
Datto. Defending Against Data Loss: Choose the Reliable Solution
When a large-scale data loss recently occurred at a backup provider, it shined…
BeyondTrust. One-Time Password (OTP) Solutions for Privileged Access
What are one-time passwords? A one-time password (OTP) is the password used…
HelpSystems. Customer Phishing Protection Couldn’t Be Easier with Agari and PhishLabs
It’s not news that cybercrime is a constant battle—large enterprises and small…
Core Impact Introduces Ransomware Simulation
Once upon a time, it was often necessary to define the term “ransomware” as…
Core Security by HelpSystems. 4 Steps to Take Following a Pen Test
Congratulations! You’ve just completed a penetration test. So what now? A pen…
Introducing Sophos Cloud Native Security
Protect all your servers, from on-prem to multi-cloud, Windows to Linux, all…