BeyondTrust. How to Protect against EMOTET – “The World’s Most Dangerous Malware”
In the summer of 2020, malware infections were on a clear rise. Many new variants were appearing, and enterprises, government agencies, business leaders, and public officials were all voicing concern. Yet, seven years after it was first discovered, the spread of the EMOTET malware was arguably most concerning of all.
Fast-forward to January 2021 – thanks to a collective effort across the globe, EMOTET is FINALLY beginning to lose the battle. Investigators coordinated by Europol and Eurojust are effectively collaborating to interrupt the EMOTET botnet, and making significant headway. With that said, the threat potential of the malware remains worth paying attention to. Read on to learn how to protect your organization against EMOTET and similar threats.
What is EMOTET?
EMOTET, often called “the world’s most dangerous malware” is a type of Trojan. It manifests either as a standalone malware, or as a delivery mechanism leveraged to get additional payloads onto the target machine. First discovered in 2014 by TrendMicro, EMOTET was initially spotted attempting to navigate through systems and steal private information.
Since then, EMOTET has gained many modifications to bolster its arsenal. For instance, newer strains can communicate with a central server to download additional and updated malware. Today, EMOTET can easily spread through the simple use of phishing emails, which contain a malicious Office document sent with eye-catching subject lines. Once opened, a macro that runs a PowerShell script within the Office document triggers and the payload malware is downloaded to the now infected system.
Despite the joint efforts by Europol and Eurojust, we are still seeing EMOTET variants, as well as other malware copying EMOTET’s techniques. MITRE technique T1047 and T1059.001 are examples of WMI and PowerShell attacks that implement two common techniques used by EMOTET.
How can I protect my organization from EMOTET and EMOTET-like attacks?
Phishing attacks are prone to a degree of success due to the persistence of poor end-user cyber hygiene and awareness. However, a number of steps can still be taken to limit the damage that attacks like EMOTET can inflict. Let’s take a look at some effective security best practices:
- First – always, think before you click. Yes, this sounds simple, but following this simple advice substantively helps limit infections over the long run. Always assess whether you trust what you are about to click on before you do!
- Train your workforce. This can be in the form of targeted security awareness training for IT administrators, or more generic training for other users to ensure there is knowledge of the risks throughout your organization.
- Update, Update, Update! It seems that every day you get an application that is wanting an update–these updates are being provided for a reason. Often the reason for the update is to provide additional security to applications that you have installed, or to address a vulnerability that was discovered.
- Ensure the security essentials are in place – Antivirus, anti-spyware, firewalls, privileged access management (PAM), etc. If you lack these foundational security technologies, attackers do not need to use sophisticated attacks when targeting you.
- Constantly work to reduce your attack surfaces and threat exposure. An end user running with more privileges than absolutely necessary makes it a fairly easy exercise for malware to infiltrate a system and propagate through a network. Removing all unnecessary privileges helps reduce attack surfaces and also restricts the ability for lateral movement inside the network.
How BeyondTrust Privilege Management for Windows protects against phishing attacks and malware
BeyondTrust’s Privilege Management for Windows product provides manifold protections against malware, phishing exploits, and other attacks. One special product capability, called Trusted Application Protection (TAP), prevents commonly used attack chain tools from being spawned by trusted applications.
TAP Policies utilize properties of the processes on the endpoint to determine:
- What the processes are
- Their relationships with other processes
When a user opens a malicious document with a payload, the TAP Policies will block the launch of the payload, protecting the user and their endpoint.
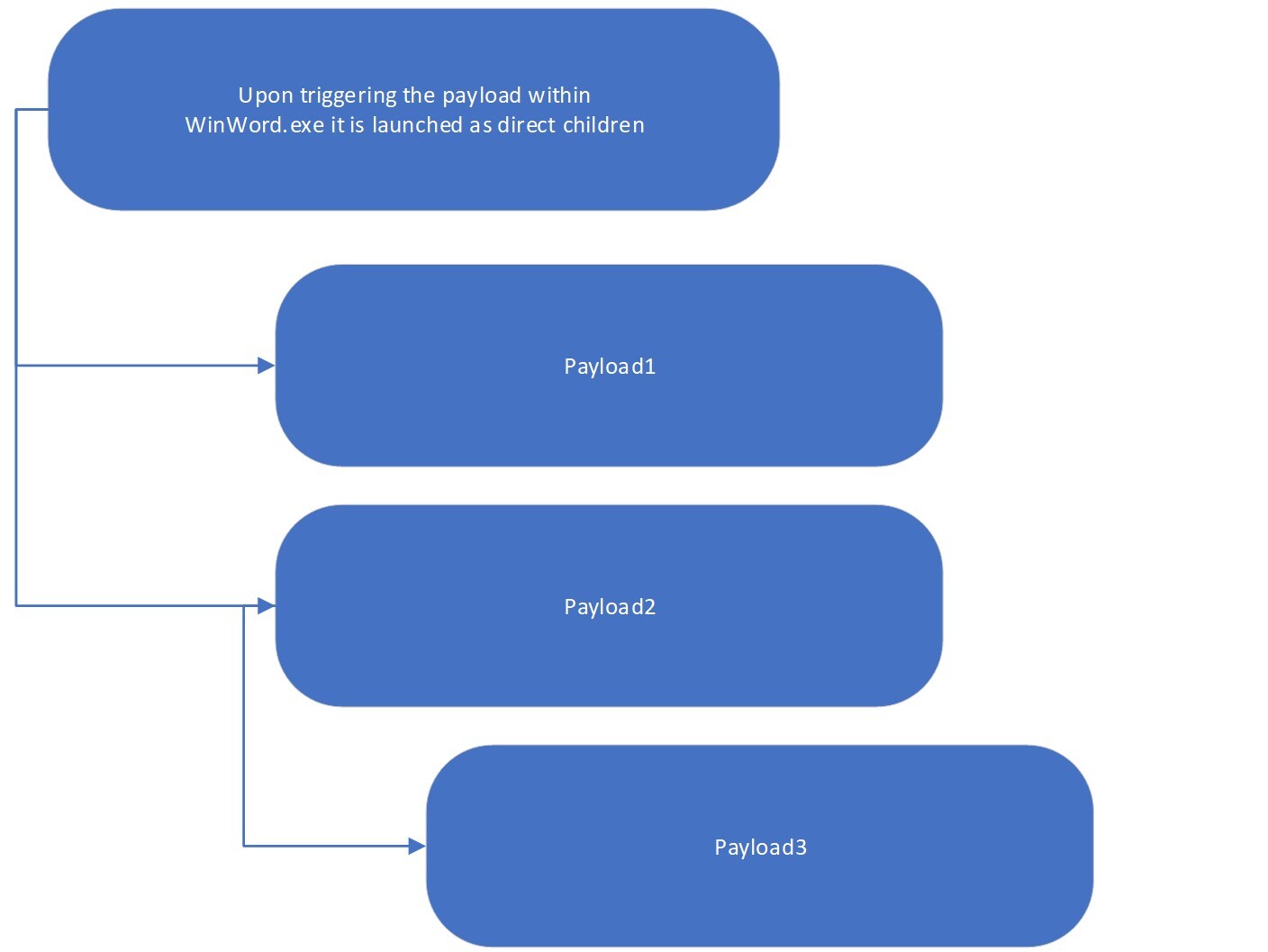
Figure 1: How regular attacks trigger payloads
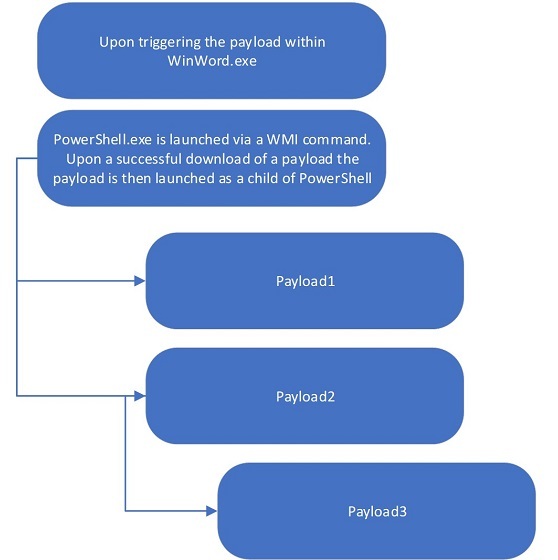
However, EMOTET can be a bit trickier than what is shown in the above figure. The EMOTET payload, a PowerShell script, is not triggered as a direct child of the trusted application. Instead, the payload is launched via a WMI call, thus, PowerShell.exe is not seen as a child of the trusted process.
This evasive method is increasingly being used within attacks as it is more difficult to track where the process originated.
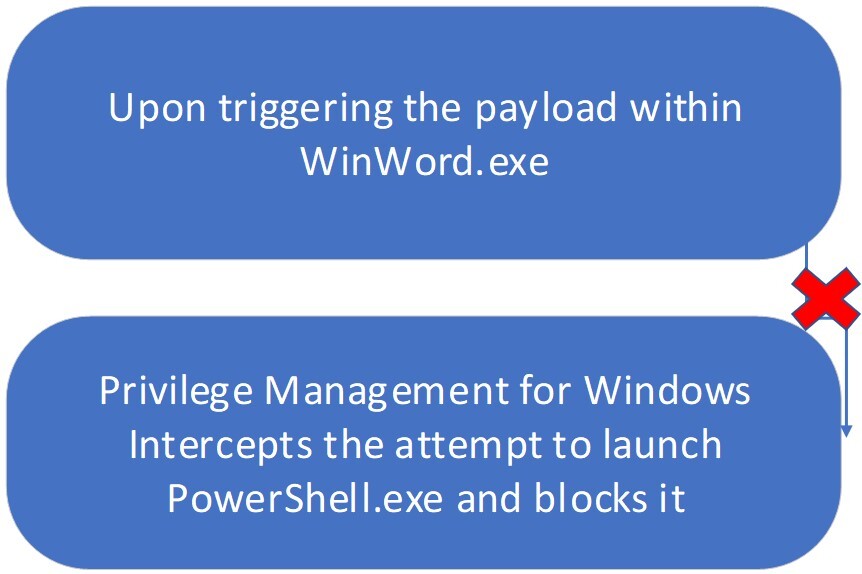
In v21.3 of Privilege Management for Windows, we added our patented functionality to help protect against these more sophisticated attack techniques, such as used by EMOTET. With our ability to track processes being created including out-of-hierarchy child processes, we can block these attacks when they occur (Figure 3).
Learn more about Trusted Application Protection & Endpoint Privilege Management.
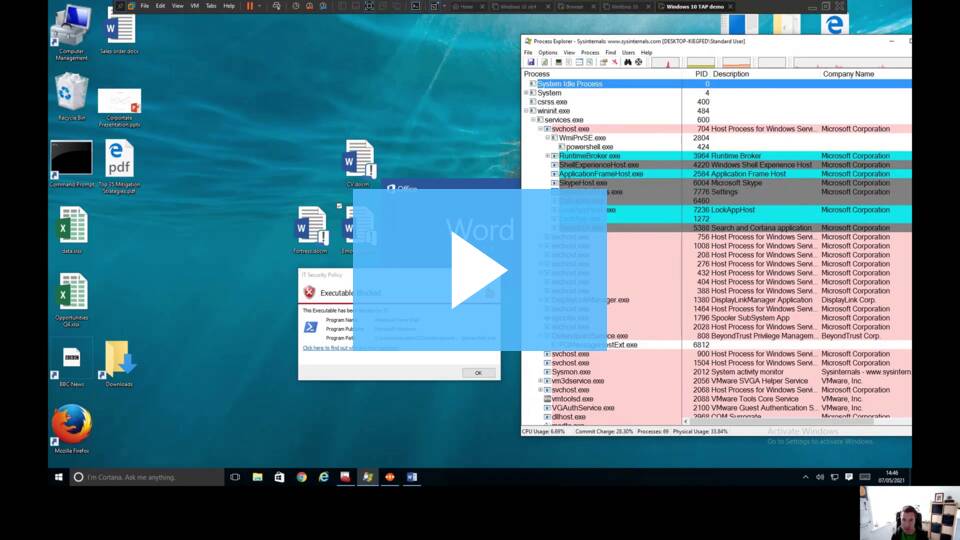
In this video, James Maude, BeyondTrust’s Lead Cyber Researcher, demonstrates how the TAP and Advanced Parent Tracking capabilities of Privilege Management for Windows prevent an attack that uses out-of-hierarchy process launches.
How to Protect against EMOTET – “The World’s Most Dangerous Malware” | BeyondTrust
Video: BeyondTrust’s Advanced Parent Tracking feature protecting against out-of-hierarchy process launches.
Source: BeyondTrust