BeyondTrust Malware Threat Report 2021: Attack Trends & Mitigations
BeyondTrust has just published our Malware Threat Report 2021, produced by the BeyondTrust Labs team, with collaboration from customers and incident response teams using BeyondTrust solutions. The report is based on real-world monitoring and analysis of attacks between Q1 2020 and Q1 2021, and also involves the testing of 150 recent malware strains against the MITRE ATT&CK Framework.
Here are a few key findings published in the report:
- Fileless threats are increasing and being leveraged in the initial attack stages until a strong foothold and persistence mechanism is established and security controls have been disabled.
- Malware-as-as-service (MaaS) is becoming a preferred threat actor model, leading to specialization in the production of malware tools that can be purchased and deployed along various stages of the attack chain.
- The MITRE ATT&CK Framework provides an effective way to distill a wide range of malware strains and cyberattacks into component techniques, which can then be mitigated.
- BeyondTrust’s out-of-the-box policies proactively disrupted all 150 different, common attack chains tested in our analysis.
- Removal of admin rights and implementation of pragmatic application control are two of the most effective security controls for preventing and mitigating the most common malware threats seen today.
Read on for some more highlights on the report, including reoccurring threat themes, and the effectiveness of privilege management at preventing and mitigating cyber threats. You can also download the full report here.
Maturity of the Malware Ecosystem
Cybercrime is a high-growth industry that is constantly evolving with regard to malware ecosystems and their economic models. Parallel to legitimate software companies and the trend towards SaaS, threat actors are shifting to malware-as-service models, with specialists emerging in different areas, including enterprise credential sales, initial access to a target organization, lateral movement capability, or payload delivery.
Today, there are often many different pieces of malware that come together in an attack. A modern ransomware attack could be comprised of multiple threat actors, tools, and platforms. For example:
- Threat actors rent the Necurs botnet and use it to distribute malicious spam.
- Spam contains malicious documents that launches Trickbot.
- Trickbot is used to harvest credentials, access emails, and for lateral movement across the network. The stolen data can be sold or used in later attacks.
- With widespread compromise of the target network, the threat actor sells backdoor access to the network to the highest bidder.
- The buyer then deploys RYUK ransomware via the Trickbot command and control servers.
As threat actors seek to maximize the disruption to organizations and extract the highest ransom payments, the ransomware model is shifting towards human-operated, enterprise-wide attacks.
Rather than create an automated worm that self-propagates across the network, the latest generation of ransomware-as-a-service (RaaS) will tread lightly, establishing a foothold in the network of a large organization. Using common penetration testing tools – such as Cobalt Strike or PowerShell Empire – they then survey the network and spread using privilege escalations to gain control of critical systems and disable security controls, before finally encrypting key systems and exfiltrating data.
PAM – A Powerful, Blended Defense Against Today’s Malware Threats
All too often, malware will not only use multiple techniques to evade detection, but will also exploit excessive privilege granted to end users to disable security controls, which completely undermines your defenses and security investment.
66% of the 58 techniques in the MITRE ATT&CK Framework either recommend using Privileged Account Management, User Account Management, and Application Control as mitigations or list Administrator / SYSTEM accounts as being a prerequisite for the technique to succeed.
Therefore, the control of privileges and application execution prevention is a key defensive measure in mitigating Cobalt Strike and tools/malware with similar capabilities, through a reduction in the attack surface and denying code execution and privileged rights.
Lab-Testing BeyondTrust Trusted Application Protection Against Top Malware Strains
BeyondTrust’s Privilege Management for Windows product is designed to eliminate unnecessary privileges, strictly control privileged access, and provide pragmatic application control to proactively reduce the attack surface. Within this product, is a unique, Trusted Application Protection (TAP) feature, which provides an out-of-the-box policy designed to mitigate common attack techniques—including fileless threats—and prevent high risk applications, such as Web Browsers, PDF viewers, Outlook, and Microsoft Office from being exploited.
Trusted Application Protection uses both privilege management and application control capabilities to prevent these high-risk applications from launching custom malware payloads. It also protects high-risk applications from more sophisticated DLL attack techniques, such as DLL injection, hijacking, and malicious DLL plugins.
To test the effectiveness of Trusted Application Protection, BeyondTrust Labs examined the attack chains of thousands of malware samples from the past year. While malware will constantly change the content of the phishing emails, re-encoding payloads to evade AV, and use new scripting techniques to hide their intent, there is less variability in the attack chains used.
As an example, a threat actor might use a range of document types and create hundreds of variants with unique file signatures. However, every variant will launch CMD, then run a script that pulls down a custom executable payload and launches it. While the document changes, the script, the website hosting the executable, and the payload may all change—the attack chain remains consistent.
For our analysis, we distilled 150 malware samples that represent the attack chains of some of the most prolific malware threats of 2020 – 2021. As you might expect, the most successful malware families tend to vary their attack chains, resulting in a higher number of samples.
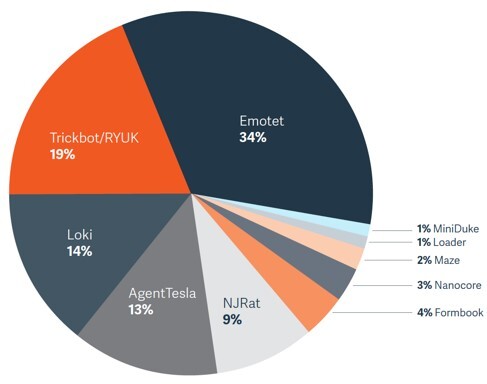
As published in the Malware Threat Report 2021, our analysis clearly demonstrates the remarkable effectiveness of endpoint privilege management, such as BeyondTrust Privilege Management for Windows & Mac and Privilege Management for Unix & Linux products, in proactively stopping these and potential future threats, that leverage similar attack chains.
With that said no one solution can be the sole basis for a strong endpoint security strategy—it takes an ecosystem of solutions working in tandem.
For more findings on how BeyondTrust can help mitigate the most recent malware strains, download the BeyondTrust Labs Malware Threat Report 2021.
Source: BeyondTrust

