BeyondTrust. One-Time Password (OTP) Solutions for Privileged Access
What are one-time passwords?
A one-time password (OTP) is the password used in a credential pair that is valid for only one login session or transaction. OTPs are used to minimize the risks of traditional, static password-based authentication by making passwords variable per operation. As an added layer of security, OTP implementations can also incorporate two-factor authentication (2FA) to help verify the identity of the individual using an additional trusted source.
What’s the benefit of a one-time password or secret?
When it comes to securing sensitive information, there are many tactics employed by cybersecurity professionals. But as we all know, information is meant to be shared. So, how do we enable that in a secure but usable manner? One effective tactic is to implement one-time passwords.
The most significant benefit of OTPs compared to unmanaged passwords is that they are not vulnerable to replay attacks. In other words, a threat actor who manages to capture an OTP used for a valid session cannot effectively reuse it since it the password is not validefor future sessions or operations. A one-time password will typically expire in minutes, or even seconds.
OTPs themselves are typically random and also not susceptible to pattern-based password attacks, nor dictionary attacks. This makes them ideal for some of the most secure and privileged activities needed within an organization.
How do one-time passwords work? An example using Password Safe.
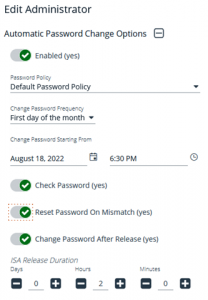 BeyondTrust Password Safe is a privileged credential management solution designed to automatically onboard, manage, and rotate passwords, and audit their use across enterprises. The randomization of individual account passwords can be configured for extremely complex passwords that are not human-readable (assuming the resource supports the complexity and length). In addition, the BeyondTrust solution allows for only a single checkout instance of a password. Once a session is complete, the password is auto-rotated until the next session request is granted.
BeyondTrust Password Safe is a privileged credential management solution designed to automatically onboard, manage, and rotate passwords, and audit their use across enterprises. The randomization of individual account passwords can be configured for extremely complex passwords that are not human-readable (assuming the resource supports the complexity and length). In addition, the BeyondTrust solution allows for only a single checkout instance of a password. Once a session is complete, the password is auto-rotated until the next session request is granted.
In essence, Password Safe allows for OTP for any privileged account session and can also be used with 2FA to provide a high confidence level of the user’s identity. “Change password after any release” is the simple feature that provides this functionality.
If you consider the benefits of OTPs and Password Safe, every customer can enhance their security posture by providing a unique password for every session and every single connection. This is a very simple security model, but incredibly effective in stopping a threat actor from compromising accounts within your environment using attacks that leverage static (or stale) passwords.
One-time passwords versus static passwords
We often work with customers who are not ready for a fully dynamic access workflow. But, at the core of this workflow, is still a centralized, audited, and access controlled solution that protects their critical credentials.
Storing static privileged credentials wrapped with modern encryption and approvals can elevate an enterprise’s security stance to meet many compliance regulations. This static storage model also facilitates a seamless phased approach to full privileged access management.
One-time passwords versus dynamic secrets
A modern iteration of a one-time password is a one-time account, aka dynamic secrets. While fundamentally solving for the same core security principles of least privilege and zero standing privileges (ZSP), the mechanics can be a bit more complex, requiring the right tooling to solve for at the enterprise level. Now, instead of just regenerating a password, a full account with account permissions needs to be considered.
Implementing OTPs – Best practices depend on use cases
There are countless use cases and methods for one-time passwords as an authtentication security control around sensitive data. It is important to understand the desired outcome for ease of access and security. The right PAM tool should help enable the balance between the two.
For more information on how BeyondTrust can help manage your privileged accounts, contact us for a demo.
Source: BeyondTrust

