BeyondTrust. Remote Access, Cloud Adoption and Digital Transformation are Accelerating: PAM is the Key to Secure and Enable It
Work from home (WFH) and remote access have accelerated the digital transformation journey, and IT’s move to the cloud. Security programs must address visibility, continuous monitoring, and a unified identity and privilege model for the multicloud environment. Privileged access management solutions are a key enabler for the cloud security strategy because they can protect core enterprise assets from increased vulnerability from the home offices at the edge to significantly reduce attacker’s ability to exploit configuration, credential, or privilege management errors.
Rope Burns & IT Security
Thinking back on those school gym classes, remember rope climbing? Or maybe swinging on a rope? Then you’ll know: ropes can be slippery, and your hands can get burned.
As businesses enabling digital transformation via accelerated cloud adoption, avoiding IT security breaches or outages (the digital equivalent of rope burns) is always a top concern. These negative outcomes can rear their heads amidst an atmosphere of too much uncontrolled change, happening too fast, to the operating environment.
A New Cloud Security Strategy
Accelerated digital transformation means accelerated cloud adoption. All those users that used to be in the office? Now they’re in the cloud. Services and applications? They too are moving to the cloud. A quick review of the Cloud Security Alliance’s top threats shows we have our work cut for us to secure cloud use.
What’s interesting about the CSA’s “Egregious 11” threats, is that many of them – such as misconfiguration, weak control plane, poor visibility, and lack of architecture, are customer-side failings. Earlier this month, I wrote about the need for Cleaning up Risk and Technical Debt spawned from ungoverned cloud adoption
The broad scope of these threats and their root cause in technical debt makes it quite clear: virtually all businesses need a new, or refreshed, cloud security strategy.
Multiple Failures to Protect Privileged Access
How were Jeff Bezos, Elon Musk, Bill Gates, and so many other IT-savvy luminaries’ Twitter accounts recently hacked and used to solicit bitcoin payments? An article from the Verge suggests that attackers “either found a severe security loophole in Twitter’s login or account recovery process or…somehow gained access to a Twitter employee’s admin privileges.”
The Twitter breach is just our latest object lesson about the importance of closing privileged attack vectors. Consider that multiple studies show Credential Misuse being the #1 cause of breaches. Behind any credential breach is an access (or privileged access) management failure. This is true because the typical user should not have access to the “crown jewels” and privileged accounts with more than the usual access should be very difficult for hackers to obtain.
Gaps in Cloud PAM
As IT’s center of gravity shifted, PAM systems have needed to evolve. Amidst the forced digitalization of the pandemic, these architectural deficiencies are no longer just limiting or annoying, they’re downright dangerous. We commonly see the following gaps in that older PAM systems have:
- Limited integration with cloud service provider (CSP) native identity frameworks or APIs
- Poor visibility into cloud environments
- Heavy server-side agent software in the infrastructure-as-a-service (IaaS) environment
- Static, or always-on, privileged accounts (also called accounts with standing privileges)
Let’s focus on the last of these gaps, to make sure everyone understands the need for…
Just-in-Time (JIT) PAM
Traditionally, privileged access is granted through a combination of static accounts and roles. For example, the powerful Active Directory domain administrator role is conferred on static accounts with a Domain Administrator group membership. As shown in the below figure’s topmost process flow, static accounts can be provisioned through identity and access management (IAM) system, or created manually. The traditional PAM system inventories the accounts that are privileged, manages access to them, and performs credential rotation.
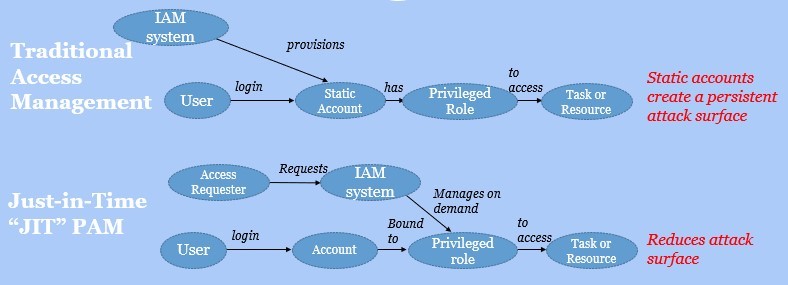
Always-on (standing) privileges versus just-in-time (JIT) privileged access
The trouble is that always-on, static accounts can become targets of opportunity. They are one of the first things advanced attackers look for as they move laterally through the victim infrastructure.
Fortunately, CSPs have provided a better way to manage privileged access. That is to bind the privileged roles to accounts only temporarily, after a request is approved. As shown in the bottom most process flow in the figure, the IAM (or PAM) system can process valid access requests and dynamically bind privileged roles to the requesting user’s account by calling an API such as the Amazon Web Service (AWS) AssumeRole. The privileged access soon expires, or is removed, reducing the attack surface available to any bad actors in the IT environment.
We need to achieve a paradigm shift from static to dynamic access grants – to just-in time privileged access management (JIT PAM).
Critical Capabilities for Cloud Privileged Access Management (PAM)
To effectively secure privileged access, credentials, and sessions across cloud environments, PAM systems need to have many of the traditional PAM features such as credential vault, credential rotation, session broker, session recording, privileged user auditing, service account support, and high availability) plus what’s below:
- Unified browser-based administration and remote session protocol support
- Authentication and authorization agility for multiple use cases, third parties, cloud environments
- Integration with cloud-native access systems
- Just-in-time access grant support
Enabling Productive & Secure Work-From-Home & Remote Access
Work from home and remote access have accelerated the digital transformation, and IT’s move to the cloud. Security programs must address visibility, continuous monitoring, and a unified identity and privilege model for the multicloud environment. PAM systems are a key enabler for the cloud security strategy because they can protect core enterprise assets from increased vulnerability from the home offices at the edge to significantly reduce attacker’s ability to exploit configuration, credential, or privilege management errors.
To learn more on updating your cloud security strategy to address the “new normal”, check out my on-demand webinar.

