Sophos Next-Gen Firewall and UTM Buyers Guide
UTM Buyers Guide gives you everything you need to find the best protection…
Solving BYOD: 5 simple tips for securing your mobile workforce
The mobile workforce are the super productive bunch. They are the ones pushing…
Sophos Expands Presence to Silicon Valley
Sophos President and CEO Kris Hagerman said, “Sophos is thrilled to join…
Sophos Unleashes Strategy to Leverage the Cloud to Simplify Security and Enhance Protection
Easy to deploy and simple to manage, Sophos Cloud gives Sophos partners and IT…
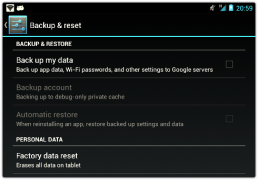
Would you tell Google your Wi-Fi password? You probably already did...
Instead of just reinstalling your favourite apps and starting afresh, your new…
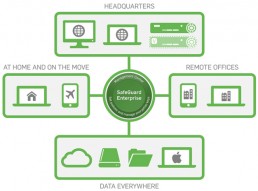
Encryption Without Compromise: The New SafeGuard Enterprise 6.1
With version 6.1 we’re addressing the two biggest issues in encryption…
What you need to know about the Bash “Shellshock” vulnerability
Although it can be exploited in some cases, the good news is that not all…
California looks to implement 'kill switch' as smartphone theft deterrent
The Federal Communications Commission reports that mobile phone theft…
Sophos: Security Made Simple
We began producing antivirus and encryption products nearly 30 years ago. Today…
WD Launches Fourth Generation WD Arkeia Network Backup Appliances
The new line up consists of four rack-mount appliance models with larger…
Latest Version of Sophos Cloud Unveiled
It features user-based management, reporting and licensing; built-in web…
WD and Baidu Partner on Cloud Service Integration
WD’s My Cloud personal cloud drives, available now in China in capacities…
Sophos Provides Support For New ‘Cyber Streetwise’ Campaign
James Lyne, Global Head of Security Research, Sophos, said: "Sophos has…
Logpoint και SIEM. Adding more dimension to the modern CCTV system
Imagine a system that can alert you when it starts to rain, not only warning to…
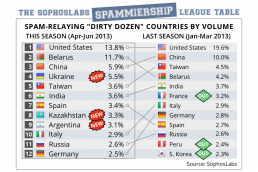
The Dirty Dozen spamming countries - introducing the SophosLabs SPAMMIERSHIP League Tables!
Likewise, the three countries that took their place in the top flight all came…
Sophos Mobile Encryption 2.2 released. Free file encryption app for Android and iOS
Download the Sophos Mobile Encryption app from Google Play for Android, or from…
Critical Infrastructure Providers Strengthen Cybersecurity by Implementing Standards-Based PKI
Recent headlines and mounting evidence suggest that cyberattacks on Critical…
GlobalSign Offers Free SSL Certificates for Open Source Projects, Helping Make the Internet More Secure
By offering this service, GlobalSign hopes to encourage the use of SSL in…
Sophos Delivers Advanced Threat Protection for the Small and Mid-Market
Developed by SophosLabs, this new Sophos UTM approach brings together multiple…
Amazing summer offer! WD Arkeia appliances come bundled with all software licences, a value of €12.000
Saving your data and increasing your bottom line just got easier. Purchase a WD…
WD Introduces New Ultra-Compact Network Storage Plus Servers, WD Sentinel DS5100 and DS6100
“WD is using enterprise-class components to build a new family of network…
OpenSSL Heartbleed, what is it and what does it mean for security?
We also found out that the Heartbleed bug is in a version of the OpenSSL…
Sophos Mobile Security for Android version 4.0 is coming – Sign up for the beta to win a prize!
Sign up for our beta program today and we’ll notify you by email when the…
'Virtual Lolita' bot imitates a schoolgirl to trap chatroom paedophiles
One of Negobot's creators, Dr. Carlos Laorden, told the BBC that past chat bots…
UTM Series appliances. Our best sellers ever!
UTM Series appliances will remain an important part of our hardware appliance…
Top 10 Reasons to Choose APV Series Application Delivery Controllers (ADCs)
Here are the Top 10 reasons to choose Array's APV Series Application…
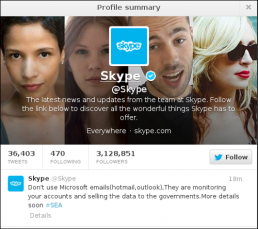
Skype's Twitter account compromised by Syrian Electronic Army
This isn't entirely surprising as the FBI had issued a warning on Christmas Eve…
Sophos Gets Tops Marks from Leading Independent Antivirus Tester
Sophos received top marks in the latest report from AV-Comparatives, a leading…
Sophos Awarded 5 Star Rating in CRN 2014 Partner Program Guide
A ‘channel-first, channel-focused’ company, Sophos continues to…