How Sophos Intercept X Advanced can protect you from Mar-a-Lago-like USB stick attacks
Earlier this week, news broke that a Chinese woman attempted to sneak a USB stick loaded with malware into Mar-a-Lago, President Trump’s main place of residence outside of the White House.
The news made international headlines due to the nationality of the alleged attacker and the location of the attempted attack.
Using an external device like a thumb drive to deliver malware is not a new attack method – it has been around for years.
But this somewhat old-school delivery mechanism is still very effective today. Why? Because many endpoint protection products only focus on “next-gen” approaches to endpoint security and skip over proven foundational techniques that have worked for years.
Those techniques include “device control” or “peripheral control” which protects external hard drives.
The USB stick incident at Mar-A-Lago is a perfect example of why you need endpoint protection that combines modern/next-gen techniques *and* foundational techniques like device control. Fortunately, with Intercept X Advanced you get both.
How does Intercept X Advanced protect against this type of attack?
Intercept X Advanced administrators have the ability to control access to removable storage devices (like USB sticks), mobile devices (iPhone, various Androids, Blackberry), Bluetooth, and other peripheral devices.
They can choose to either block the use of peripheral device types altogether, monitor devices, allow in read only mode, or block/allow specific devices.
If a person was able to sneak a USB drive into an environment, they would receive a message similar to this when trying to use it:
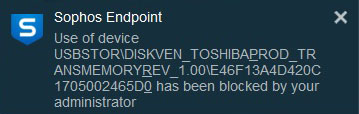
But that’s not it…
Even if this feature had not been enabled, Intercept X would be able to detect the malware before it executed using the industry’s best malware detection engine, powered by deep learning technology. Find out more about Intercept X Advanced here.
You can read the original article, here.

