Sealpath. Against the New Generation of Ransomware Attacks, How to Protect your Data with Encryption (Part 2)
Ransomware attacks can be mitigated with some security measures and techniques, but in terms of publishing of sensitive data, only data encryption protection can help you. Find out in this article how to protect your sensitive data with encryption, steps for an effective encryption strategy and what to encrypt.
Taking back control of your data through Encryption
It is established that encryption is important to secure your data, but that is not the only solution. It is not only important for modern security but is also core to modern computing if you want to excel in an internet driven environment. In fact, it is more important that you have an effective information policy where big tech companies and third-party providers allow you to cloud compute, and store and share vast amounts of information online; it is only essential that you encrypt all that data before using these services if you manage sensitive data.
It is not only important to fully evaluate and prioritize which data needs to be enabled to be accessed and stored, it is also crucial that you fully encrypt all of the documents and communication files before putting them online. This way you can greatly reduce the vulnerability of your organization and/or company’s potential of a data breach by big cybersecurity thieves.
Who is at Risk?
Despite the incidences of frequent cyber attacks, data breaches and identity thefts, IDC reports that only 3% of those information leaks and data breaches was encrypted and protected. This means that 97% of that data was not encrypted and highly exposed, with only 3% unusable to the cyber thieves due to being encrypted and inaccessible despite being stolen.
One of the greatest responsible motivator of wide spread of ransomware is to make money or gain profit through ransom. As far today’s scenario is concerned, the objective of ransomware is damage, destruction, harming victim at any state and yield as much money as possible either by hooks or crooks.
Some people are more at danger than others:
- Corporate or Business Sector are most favorable target for ransomware initiators due to the presence of huge amount of confidential data regarding its consumer, sales, purchase, ledgers, journals, quotations, taxes etc. Loss of such documents can cause the whole business to shut down or bear major losses. Thus, corporate sectors opted to willfully pay ransom instead of suffering setback. The proceedings of World Congress on Engineering and Computer Sciences estimated that out of all victims, around 46% of corporations are targeted, out of these 88% were not using encryption.
- Public or Government Sector. This mostly comprises of educational institutions, power corporations, telecommunications, law enforcement wings, hospitals, banks, transportation and all those establishments that have direct impact on public. The risk of not being encrypted comes from hackers affecting such institutions, increases the probability of getting ransom because upkeep and maintenance of the offline digital copies of huge pile of data is difficult and denial to pay ransom will lead to setbacks in terms of minimum 3 to 6 months, i.e., another big deal of nearly a fresh start. Similarly, infecting government sector fulfil two major objectives of crooks, one to ensure the payment of ransom and if not, then steal the data regarding defense, citizens, budgets, policies etc. and sell it for money over dark net. Hence, encryption of all these data can not only save the organizations and public departments from paying huge amounts of ransom, but also prevent the theft of piles of data that could otherwise set back public or organizational affairs by upto 3 to 6 months or even more!
- Home Users or Individuals are softest targets of ransomware due to their least fluency with technical aspects of computers. Although a home user generally does not have huge amount of data compared to corporate sector and not related to public concerns but still have extreme significance to its holder that includes reports, projects, pictures, game files, emails, credit card information, online shopping behaviors, etc. Extortion and pressure of ransom payment further increased by eradication of any backup files and disabling of system restore just before commencement of encryption of files by ransomware.
Steps for an effective encryption or data protection management plan
It is important to formulate an encryption or protection plan by following through the three critical questions to allow yourself control over which data to encrypt and protect:
- Analyze which data needs to be encrypted: Since it’s your data and your company, it is important that you carefully analyze, evaluate, and prioritize which date needs to be encrypted the most. For instance, this could include personally identifiable information (PII) and any trade secrets that would be harmful if leaked.
- Having a document protection plan: Having encryption is the first step and having an encryption is the last and second most crucial step in your data protection. It is important that you decide what happens with your data while it is in transit and while at rest. These require different levels of protection and you can fully control what happens when. For instance, you can choose to destroy a file if it is shared beyond what you initially provided access for. But, for this to work, you need to have that type of encryption embedded in your file beforehand.
- Establish solid and easy-to-manage protection policies: It is a busy world and you may often get too caught up in day-to-day affairs of your company to bother with data breaches of previous documents. However, you can choose types of protection policies management plans to automatically keep up with your data while it is at rest and whenever, wherever it is accessed or shared online. This way you can assess your encryption performance regularly to get clear of any serious data breaches.

If you want to learn more about a more detailed approach and deploy to protect your corporate data through a data-centric security approach, read this article.
Knowing what to Encrypt and How much to Encrypt?
Organizations or public sector departments and businesses must be told what information should be safeguarded when encrypting files or folders on file servers or cloud repositories. It’s also critical to use automation to make file protection easier, especially when encrypting folders or safeguarding data in information repositories. In order to avoid spill of privacy, disclosure of confidentiality and enhance a secure transmission of message between two parties the encryption tools are designed to provide safety and ensuring security goals during communication. Take for instance, the Zero Trust Security Model, which focuses on the ‘layer’ protection, on the premise that since every data is so mobile online, it is important to assume that no one or nothing can be trusted.
IRM (Information Rights Management); beyond encryption
IRM systems deal with the challenge on what happens with data once it is in transit or has left the perimeters. Also known as E-DRM (Enterprise Digital Rights Management) or EIP&C (Enterprise Information Protection & Control, it uses a highly sophisticated and effective form of cryptographic protection that applies to files that are travelling and provides protection wherever they transit. The IRM’s system approach is to apply a layered protection to the data that can be controlled even if it is no longer in the network, whether it is in a cloud, on a mobile device, etc.
If the data reaches someone it shouldn’t of whom you consider shouldn’t have access to it, you can revoke the access remotely. You can set expiry dates for documents. Give users more or fewer permissions in real time (Edit when before they could only Read, or restrict the permission to read-only if we don’t want them to edit or print). The ease with which this type of solution may be implemented means you can start using it right away and encrypt and regulate important data that your firm controls internally or with third parties.
One of the most critical aspects of this technology is its ability to be made simple to use so that non-technical people can manage protected data as if it were unprotected data. One part of encryption is allowing end users to be at ease in assessing and using, sharing, editing, transferring their own data without having technical difficulties and know-how of cryptography. It is done by making it compatible with the apps that users use on a daily basis, such as Office, Adobe, and AutoCAD, as well as the information repositories that companies often use, such as File Servers, One Drive, G-Suite, Microsoft Office 365 Cloud applications, SharePoint, Drop Box, and so on.
Hence, depending on the vulnerability of the data, the extent of damage the leakage or theft of which document can have on an organization, you can choose to apply different levels of protection. For instance, if you are sharing confidential information about a new tender with your business partner, you may allow it to be shared with only specific parties, departments with only view-only permissions – beyond which if accessed, the files could not be assessed and if tried to decrypt, would be of no use to potential competitors.
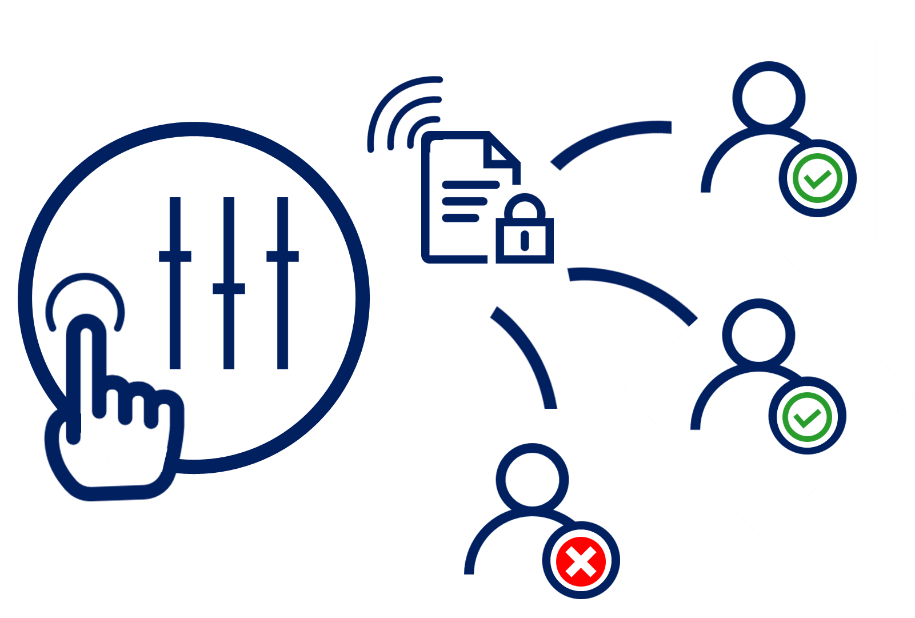
On the other hand, you might want to limit access to your company’s data that may harm your company, employees, customer base and business partners, if stolen. You can put a minimal protection but with certain levels of access permission. You can choose exactly what happens with which type of data, develop a ‘protection in use’ policy of the encryption and not just a protection in rest or transit. Also, although many organizations and public departments may have pinpoint documents labeled as ‘public’, ‘private’, ‘confidential’, ‘internal use only’, etc, it is more evident on paper than online. Being able to encrypt them according to the levels of classification on paper would be the real win for these organizations. IRM integrated with data classification tools allow you to automatically protect classified or labelled data with a specific IRM protection policy.
Takeaways of Protecting Your Documents Through a Data-Centric Security Approach
It is established that encryption involves a data-centric security management strategy to protect the collective interests of an individual or organization, employees, customers, partners and more. Some of the advantages of having a multi-layer encryption-based protection based in a data-centric security approach for your online data may include:
- Protection of sensitive documents without relying on user actions.
- Ensuring protection of data whether information is travelling outside network perimeter, being accessed by an outsider or while it is in transit, at rest and in use.
- Control what users can do with your documents (View only, copy & paste, edit, print, etc.).
- Monitor, allow or disallow access regardless of where your data is.
- Revoke access to sensitive information even if you provided access permission before.
- Protecting your intellectual property rights by having full control of your data, hence making it almost impossible to be stolen by competitors and imprinters.
SealPath allows you to develop an effective management system for all your sensitive data you want to protect with effective protection, monitoring, and automation systems. You can ensure efficient protection using an integrated IRM (or E-DRM) model to ensure protection of your data in use, at rest and in transit, without having to worry about theft or paying ransoms due to theft.
Source: Sealpath

