Data is one of the valuable commodities shared by all organizations regardless of size, location, or the industry it operates in. Today, businesses hold more data than ever, with large volumes being generated, stored, sent, and received. There is more regulation to govern data, requiring organizations to protect it from unauthorized access. There are also more data breaches, resulting in large fines, and the loss of customers and reputation. It’s a challenging environment, especially in light of remote work being a permanent reality for many organizations whose employees need to securely collaborate from anywhere.
To Secure Data, Visibility is Key
In a recent HelpSystems study, CISOs agreed that data visibility is their biggest cybersecurity weakness. How can organizations possibly govern data effectively if they don’t know what data they have, where it lives, how it is shared, or who has access to it? Understanding this information significantly improves a company’s ability to manage and control its data and helps them select the right technology to ensure it remains protected and secure throughout its lifetime.
Traditionally, data security focused on controlling the infrastructure – and the networks and devices that operate within it – locking data down and tightly controlling who has access to it. While secure, this makes collaboration very difficult and leads to poor productivity.
Modern data security solutions focus on protecting the data itself. This means that organizations can take full advantage of cloud-based applications and operate effectively within hybrid IT environments, as the technology secures the data no matter where it resides or how it travels. The data security ecosystems work to automatically minimize both internal and external threats – be that an employee who accidentally shares sensitive data with the wrong person or a malicious actor looking to release malware when an employee opens an inconspicuous file.
The HelpSystems Data Security Solution
HelpSystems understands that the challenge of data security isn’t something an organization can solve overnight. Data security projects take time to implement, and a modular solution, one where the organization can implement a component, get it working and adding value, and move on to the next, offers the greatest level of flexibility. HelpSystems’ Data Security Suite offers multiple security solutions that can be used independently or together to benefit from economies of scale. Each solution adds a layer of security to the data, from the time it is created to when it reaches its destination, and beyond.
How it Works
Here’s an example of how the Data Security Suite works when the modular solutions are used together as one product suite (see below). Each solution has its own set of capabilities, here we are highlighting just some of the functionality available.
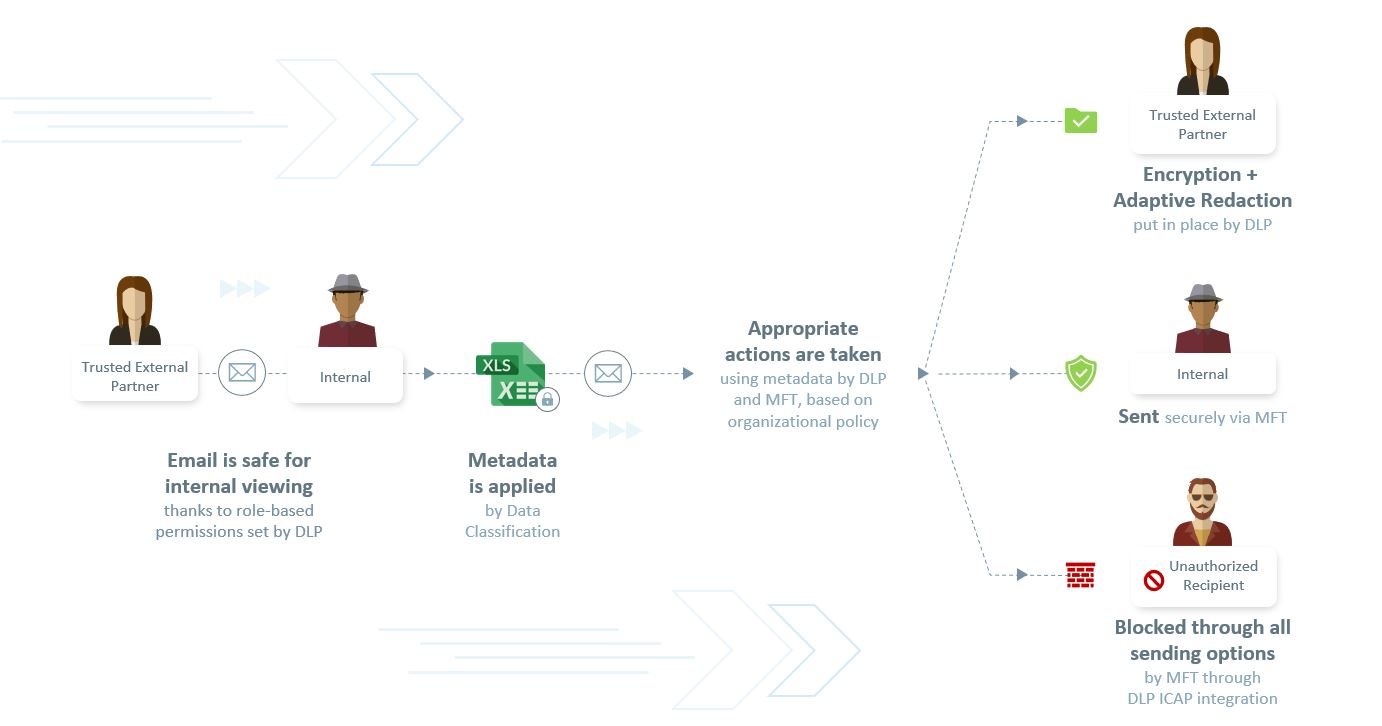
Data enters the organization and role-based permissions help ensure it is safe for internal viewing.
When this data is saved (in this example, as an XLS file), it is classified according to its sensitivity and value to the organization. Metadata labels allow the other data security solutions within the ecosystem to understand that the data is sensitive and requires further protection based on the organizational policy. Classified data may include customer or employee information, intellectual property, financial, or contractual information.
When the data needs to be securely transferred via email or the web, its content is inspected. Metadata provides the information needed to transfer the data compliantly.
The solution also checks to see if the person sending/receiving the data is authorized to do so, and if they are, encrypts it to ensure safety. If the data is not classified yet still contains sensitive information, such as credit card numbers or personally identifiable information (PII), the content can be automatically blocked or redacted.
Finally, data that is approved per the organizational policy to be shared internally or externally is securely transferred, regardless of file size.
The Solutions That Power Helpsystems Suite Include:
- Data classification
- Data loss prevention (DLP) and email security
- Managed file transfer (MFT)
- Encryption
- Secure file collaboration
Securing Valuable Healthcare Data
Here’s an example of where the HelpSystems Data Security solution has been implemented over time to help protect valuable healthcare data sent and received over email:
A healthcare provider needs to remain compliant with HIPAA and safeguard the medical data it shares between hospitals and insurance organizations.
Phase one saw the implementation of the DLP solution to automatically ensure that medical data is only shared with those authorized to receive it. The solution recognizes any sensitive data within emails and, depending on the recipient, can encrypt, block, or redact the content to ensure regulatory compliance. The valuable data held by healthcare providers makes them prospective targets for malicious actors looking to exfiltrate the data, so the solution also inspects and ensures that any hidden data or malicious malware is also automatically removed providing further protection against data breaches.
Phase two saw the implementation of data classification, allowing the healthcare provider to further enhance its compliance through the correct treatment of any classified data.
Protecting Highly Confidential Information
Where an organization needs to share highly confidential information on a regular basis, a managed file transfer (MFT) solution offers a secure and convenient way to transfer large files. The MFT solution can secure the sensitive data often shared by financial service organizations, law firms or legal departments within large enterprises, such as documents, contracts, and letters, and ensures the information remains encrypted while in transit.
If additional security is required to retain control after the data is sent or received, then further access control policies can be applied that stay with the data throughout its lifecycle. Secure file collaboration ensures that confidential data can be tracked, audited, and revoked at any time, no matter where or how it travels.
Ready to Start Your Data Security Journey?
If you’d like to see the tools within our Data Security Suite in action, watch our short six-minute demo video. The video shows how our solution can automatically redact sensitive PII data from emails and how it reads the metadata of classified information to apply the appropriate policy.
Source: Boldon James
Contact us to find out more about our solutions
Give us a call
+30 210-5914326
+30 211-8000330

