Εργαστείτε εξυπνότερα
Ο στόχος της Cherry είναι απλός: να βελτιώσει τη λειτουργία της επιχείρησής σας με ορισμένες από τις κορυφαίες λύσεις λογισμικού στον κόσμο. Οι λύσεις της εταιρείας καλύπτουν τεχνικές ανάγκες σε ένα ευρύ φάσμα βιομηχανικών κλάδων και τομέων, από τη χρηματοδότηση έως τη δημόσια πολιτική. Μπορείτε να βρείτε ενεργές λύσεις της εταιρείας σε μερικές από τις μεγαλύτερες Ασιατικές εταιρείες και κυβερνητικά ιδρύματα.
Cherry ιδρύθηκε το 2020 και συγκεντρώνει κορυφαίες τεχνικές λύσεις από κορυφαίες εταιρείες λογισμικού της Νότιας Κορέας. Βοηθούν τις επιχειρήσεις να αναπτυχθούν αξιοποιώντας, συνδυάζοντας και συντονίζοντας την παγκόσμια εμπειρία δεκαετιών της ομάδας της Cherry με τη γνωστή καινοτομία και τεχνογνωσία των παγκόσμιας κλάσης προγραμματιστών της Νότιας Κορέας. Η Cherry στοχεύει να παρέχει 100% κάλυψη – αν έχετε οποιαδήποτε ανάγκη ή απαίτηση σε τεχνικό επίπεδο, η εταιρεία είναι έτοιμη να την αντιμετωπίσει.
Εργαζόμαστε μαζί, για να εργάζεστε καλύτερα
Λύσεις Κυβερνοασφάλειας
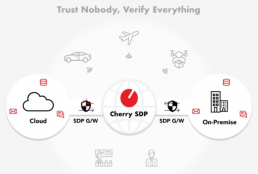
Cherry SDP
Improve your network security with Cherry’s Software Designed Perimeter that trusts nobody and verifies everything.
Realize the “Black Cloud” of perfect SDP security with world’s first solution combining SDP and NAC.
Operate free of security concerns with our open network security solution with a user ID-centric design to improve the limitations of existing Network Centric Security.
VPNs: a thing of the past?
Network security is growing increasingly important, especially in the age of COVID-19, when more and more people are working from home outside of company networks.
However, legacy network access control such as VPNs are coming under fire for a number of serious shortcomings:
- Increased cybersecurity threats
- Lack of control or visibility
- Expensive and complex
Software Defined Perimeter
Unlike VPNs, SDPs provide centralized network access control, are highly scalable, offer identity-centric user authentication and guarantee enhanced security with no lateral movement. The motto of an SDP is “trust nobody, verify everything” – all users are authenticated and authorized, and all devices are verified.
Cherry SDP provides
Cherry SDP connects communications securely outside the company, while controlling applications associated with “privileges granted to users,” allowing individuals and businesses to operate free of security concerns.
Control over network access devices
Prevent unauthorized or unregistered devices (laptop, desktop, mobile, IoT) from starting connections by SDP authorization.
Promiscuous network access restrictions
Minimize network attack potential. Prevent malicious users or software from detecting vulnerabilities. Restrict access to specific services. Refuse segment or subnet network access.
Risk-based policy support
Cherry SDP makes access decisions based on a variety of risk criteria, including threat information, malware proliferation and new software.
Connect anything
Connect to the IT services your employees need without paying administrative or additional hardware costs.
Control over network access devices
Control programs and devices that can access certain services by specifying them, preventing malicious users or malware from connecting to the resource.
Functions
Secure your network. Do business anywhere in the world with unlimited space. Control IoT devices and save money through reduced infrastructure costs. No dedicated line needed!

Server Stealth
Hides network information to make it difficult for attackers to identify targets.

DDOS attack prevention
Blocks transmission of non-authorized packets through use of Single Packet Authorization (SPA)

Dynamic Firewall
Whitelist-based firewall permitions block access in real time.

App Binding
SDP communication is possible only for applications registered by the administrator.

Safe Networking
Provides secure network by IPSEC secure tunnel communication.
Cherry DLP
“The best way to prevent data leakage”
The dramatic increase of remote work ended up giving more attention to cybersecurity. Data exchange through various devices and networks of communication expose the company and personal data. The “attack surface” of your company gets larger through these interactions. The more data to steal, the more data there is to protect.
Cherry DLP monitors and records each data movement from the endpoint to the network. Confidential and personal data is safe with Cherry DLP.
Endpoint DLP
“Discover, Monitor, Prevent Sensitive Data Leakage”
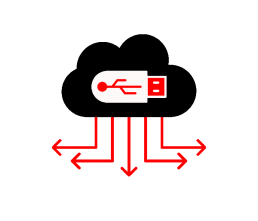
Cherry DLP prevents copies and transfers to USB, Printers, Wi-Fi/Bluetooth, and applications. Cherry DLP offers data validation checks and context identifiers. Cherry DLP secures data inside by monitoring. block-copying, saving, downloading confidential data files based on a set-up of rules and policies.
Network DLP
“Blocker at the network gateway”

Cherry DLP detects and prevents the upload of sensitive data through your network with real-time logs of in and outgoing data. Then, the SSL/TLS traffic decryption function monitors data in motion by tracking data through Email, Cloud Services, IM, SNS/TLS, and SNS. This process is effectively done with a policy(rule)-based setting.
Cherry DLP provides
Compatibility with the latest software and protoco
Cherry DLP takes a sensitive approach to customer needs and developmental proposals. The lab develops and updates patches compatible with emerging software or protocols.
Global Compliance
To fulfill privacy compliance requirements (regular expressions), such as GDPR, Cherry DLP provides the various patterns that conform compliance and keeps updating in accordance with the new regulations.
Control and deploy with effortless precision
Cherry DLP guarantees the efficiency of time, cost, and functionality by operating both EDLP and NDLP on a single console. Cherry Administrators can identify and manage data movement within a single page.
Approval Process
For business purpose, users can make exceptional file transfer through the approval process. File transfer is available after getting permission from the approver, and all actions leave logs on the console.
Customize Consulting Service
Easily edit policy settings and add custom patterns through detail and supportive Cherry DLP consultation. Cherry DLP consulting is a key mechanism for companies to meet complex and diverse global compliance.
Cherry DLP Life-Cycle
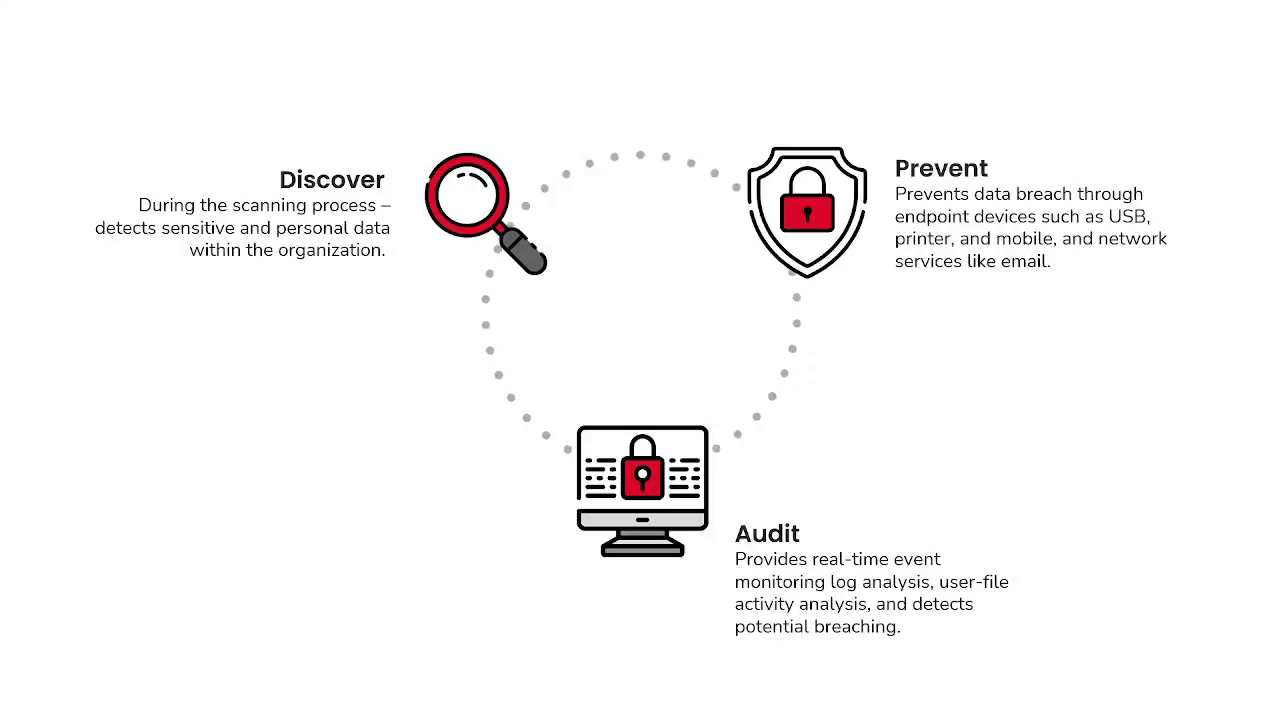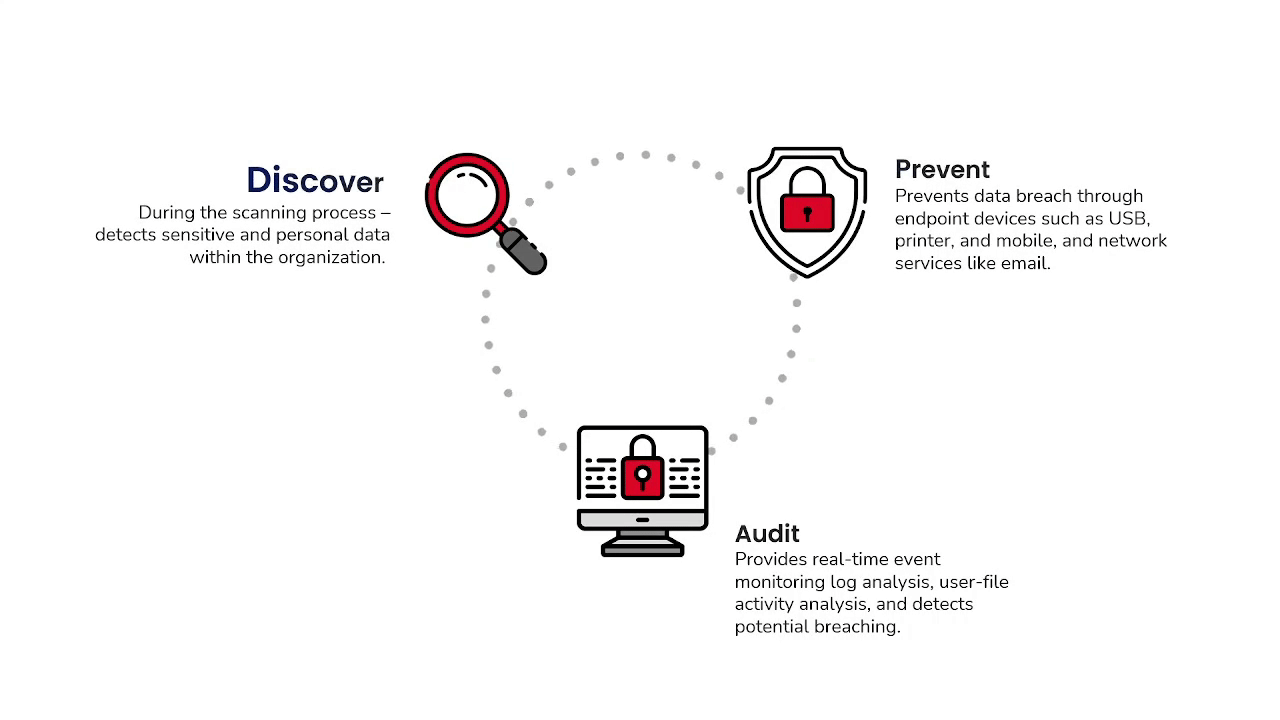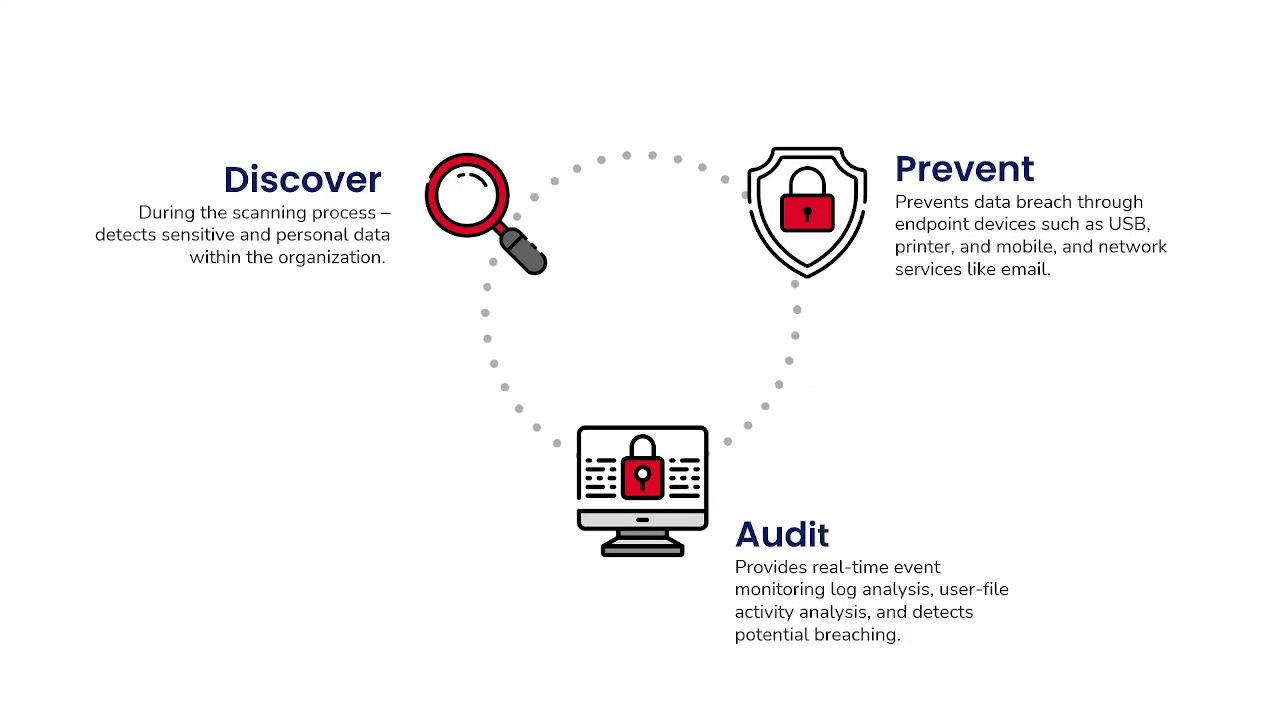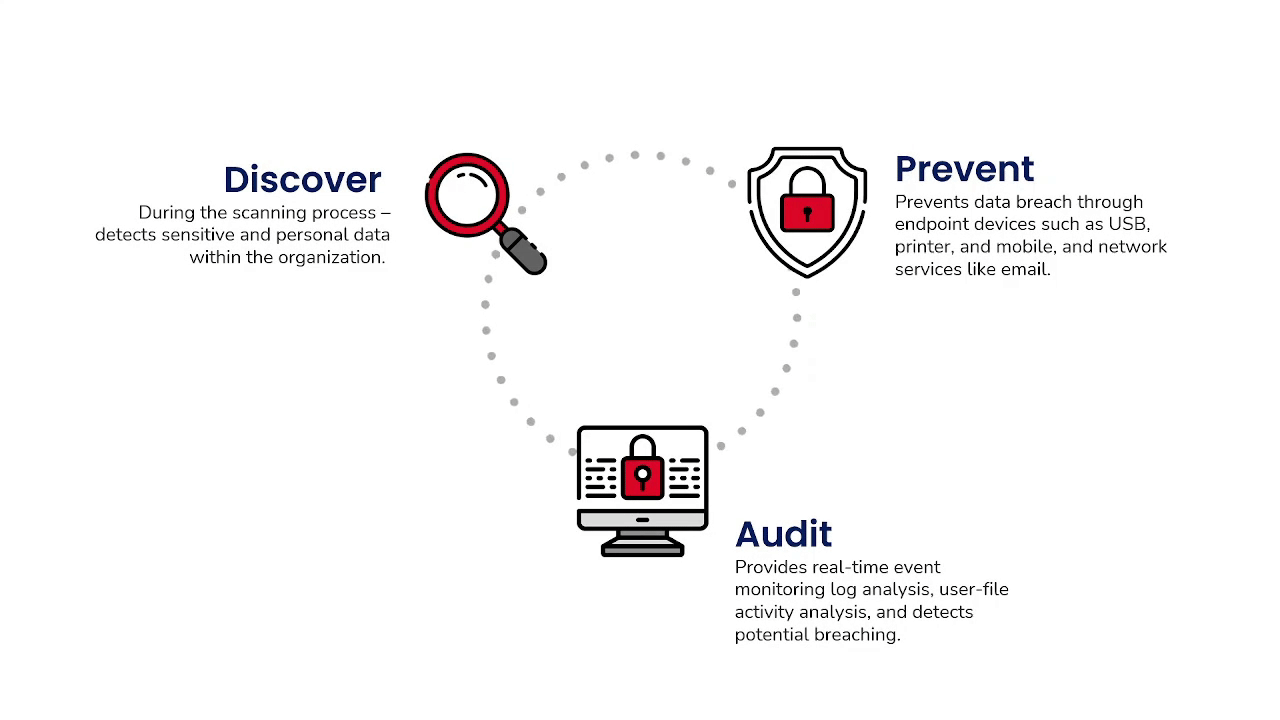
Performance Management
Cherry DPM
Manage your database performance in real time and respond to problems immediately, whenever or wherever they occur.
Korea’s leading database performance management solution lets you proactively monitor your databases, quickly recognize problems and effectively analyze bottlenecks.
Over 450 clients in 29 countries with 4,000 database servers use Cherry DPM, including AT&T, Samsung, LG Electronics, Hyundai, Toyota, Fujitsu and China Telecom.
Diagnosing the exact cause of a database problem is actually more important than solving it.Unfortunately, users now view a lot of data in different environments for different reasons. Database varieties have proliferated, too. All this makes identifying database problems very difficult.The costs of database failures can be enormous. Small errors can shut entire factories down, causing massive losses in a short time. Identifying database problems quickly – before losses mount – is critical.
Seeing everything, any time, any place
Cherry DPM is a specialized, proactive tool for managing database performance. It is designed to increase management efficiency and system operations through advanced features such as real-time monitoring, historical data logging, diagnosing, analyzing and tuning.
Monitoring
– Real-time monitoring
– Comprehensive dashboard
– Drill down traceability
Analyzing
– Real historical records
– Bottleneck/wait event analysis
– Analysis of one-second data

Visualizing
– Datapath view
– Hotspot view
– 2D/3D dashboard
Real-time monitoring
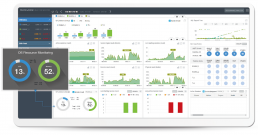
Cherry DPM collects performance logs of all running databases in real time, providing instant alarm notifications and accurate post-error analysis.
Even when your database hangs, monitor it with Cherry DPM’s DMA and API call methods. Check the operating status of the system in real time and react immediately to issues.
Cherry AMP
Get in-depth insights to make your applications available anytime, anywhere.
Observability of application performance is not an option for your businesses. In a multi-cloud application environment, customer expectations around digital experience are extremely high. It is critical to monitor application performance at all stages to provide your clients better user experience.
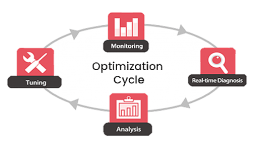
How Application Performance Monitoring (APM) solution works
- Monitor the entire application by tracking the most critical application performance monitoring metrics
- Identify and alert errors and the source of issues in real-time
- Analyze the problem with diverse performance analyzer
- Optimize application performance quickly referring to an insight from the solution
Why Cherry APM?
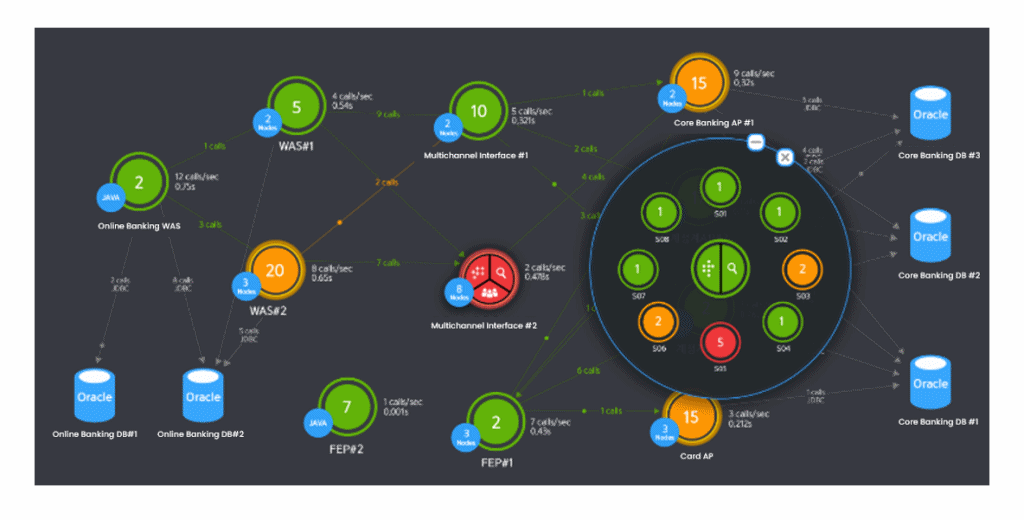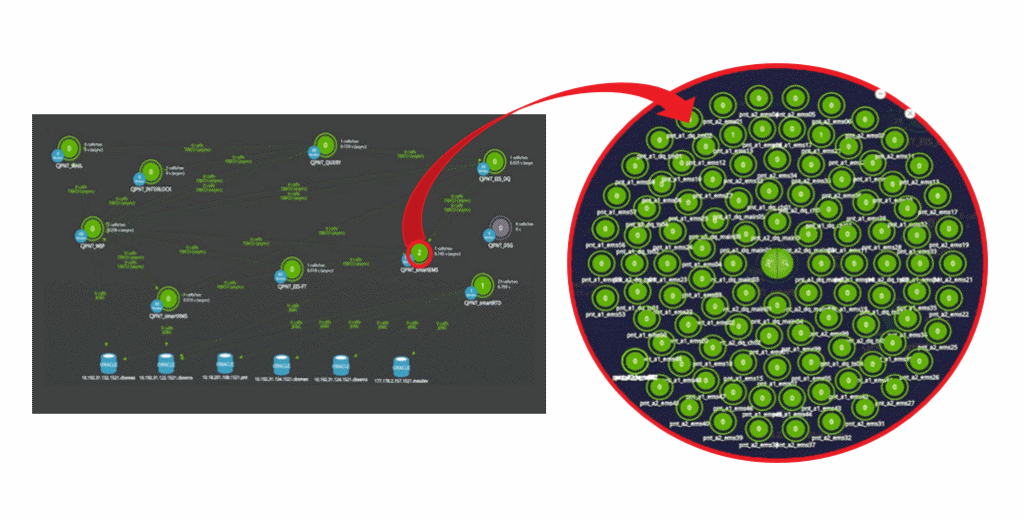
End-to-End Transaction Processing Flow
- Monitor End-to-End transaction from End User, Web, WAS, and
Database to External Agency with a consolidated topology view - Pinpoint performance issues automatically from each tier in real-time
- Monitor active response time between each transaction
- Provide an alert when there is critical performance diagnosis data
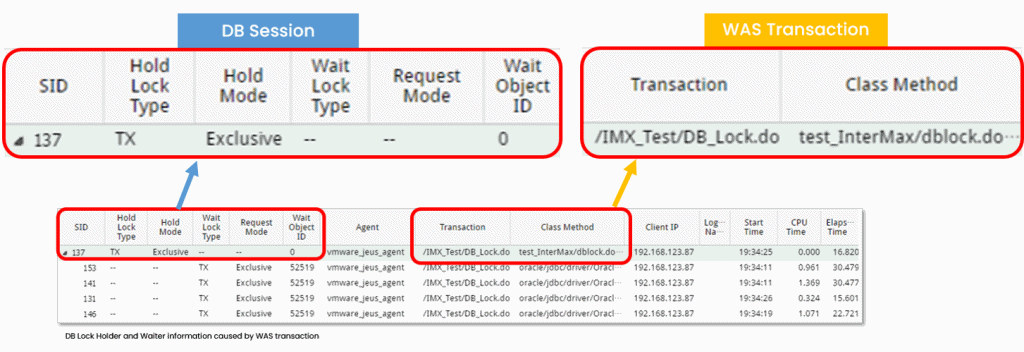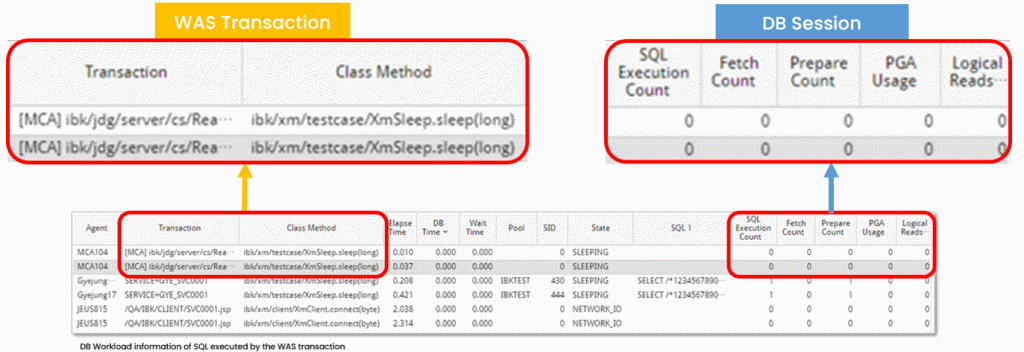
Web Application Server(WAS) Transaction – DB Sessions 1:1 Match
- Provide in-depth insights with integrated information of WAS-DB for each transaction
- Identify DB session issues connected to WAS transaction quickly with DB Lock Holder and Waiter information
- Monitor DB session performance by collecting DB Elapsed time, Workload, and Wait status informatio
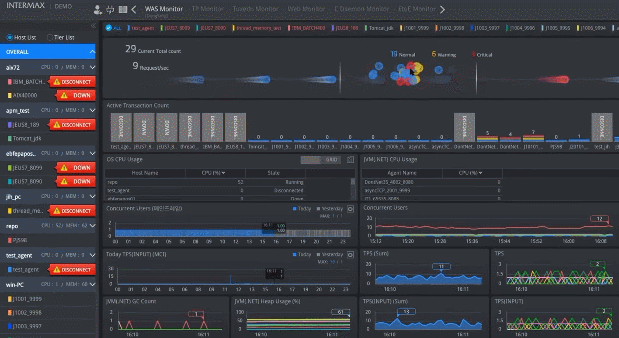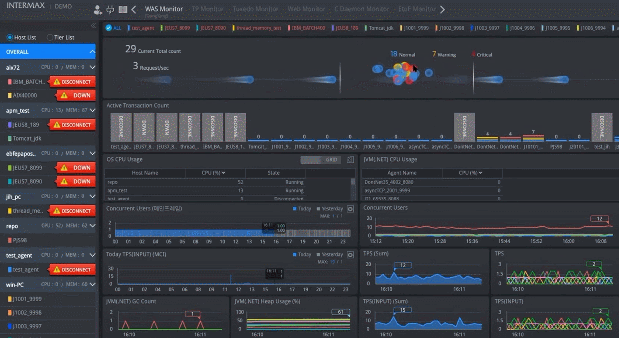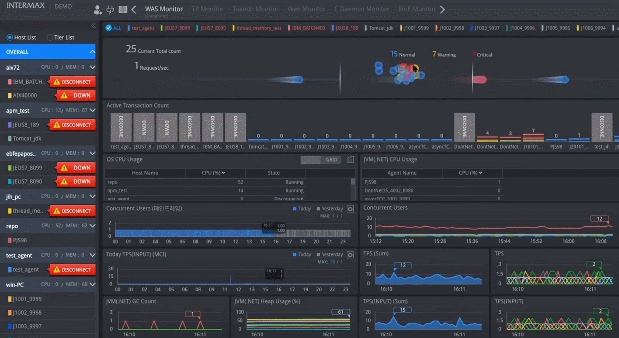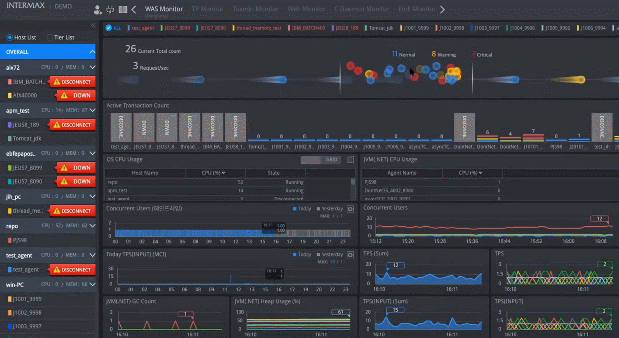
Real-Time Monitoring
- Monitor End-to-End transaction from End User, Web, WAS, and
Database to External Agency with a consolidated topology view - Pinpoint performance issues automatically from each tier in real-time
- Monitor active response time between each transaction
- Provide an alert when there is critical performance diagnosis data
Cherry APM provides

End-to-End Performance Monitoring
Help to find quick resolutions for system failures by tracing end-to-end transaction processing information
RegularReport
Provide various types of report by indicators daily, weekly, and monthly to give you an insight for a future performance trend

Performance IssureAlert
Notify the failure immediately via SMS and e-mail. Support to analyze and resolve the exact cause of problem quickly
WAS-DBIntegration
Identify simultaneous information of WAS transaction and DB session in real-time

Real-TimeMonitoring
Collect the real-time status for all nodes performing transactions

CustomizableDashboard
Make your own dashboard simply with drag & drop for the better UI configuration

Memory LeakTracing
Investigate each transaction and memory size of the object used to detect memory leak






















